Topics on this page
Trend Vision One extended detection and response (XDR) network isolation
Network isolation lets you isolate potentially compromised endpoints from the rest of your network using the Trend Vision One extended detection and response (XDR) interface.
If you connect your agents and relays to the primary security update source via a proxy, network isolation automatically uses the same proxy settings.
Requirements
- Install an agent (version 20.0.0-2593 or later for Windows or Linux; version 20.0.0-158 or later for macOS)
- Register with Trend Vision One extended detection and response (XDR)
- Forward security events to Trend Vision One extended detection and response (XDR)
- Enable Activity Monitoring
Workload Security uses an IoT mechanism to transmit messages and events to Trend Vision One XDR. If you need to restrict the URLs allowed in your environment, configure your firewall to include the Event Channel - XDR Activity Monitoring FQDNs from the Workload Security URLs table.
Isolate endpoints using network isolation
To isolate endpoints using Network Isolation:
Trigger network isolation
After identifying the endpoint to isolate, you can trigger network isolation from one of the following:
From the Trend Vision One Search App  :
:
Right-click on the endpointHostName for the endpoint you want to isolate and select Isolate Endpoint.
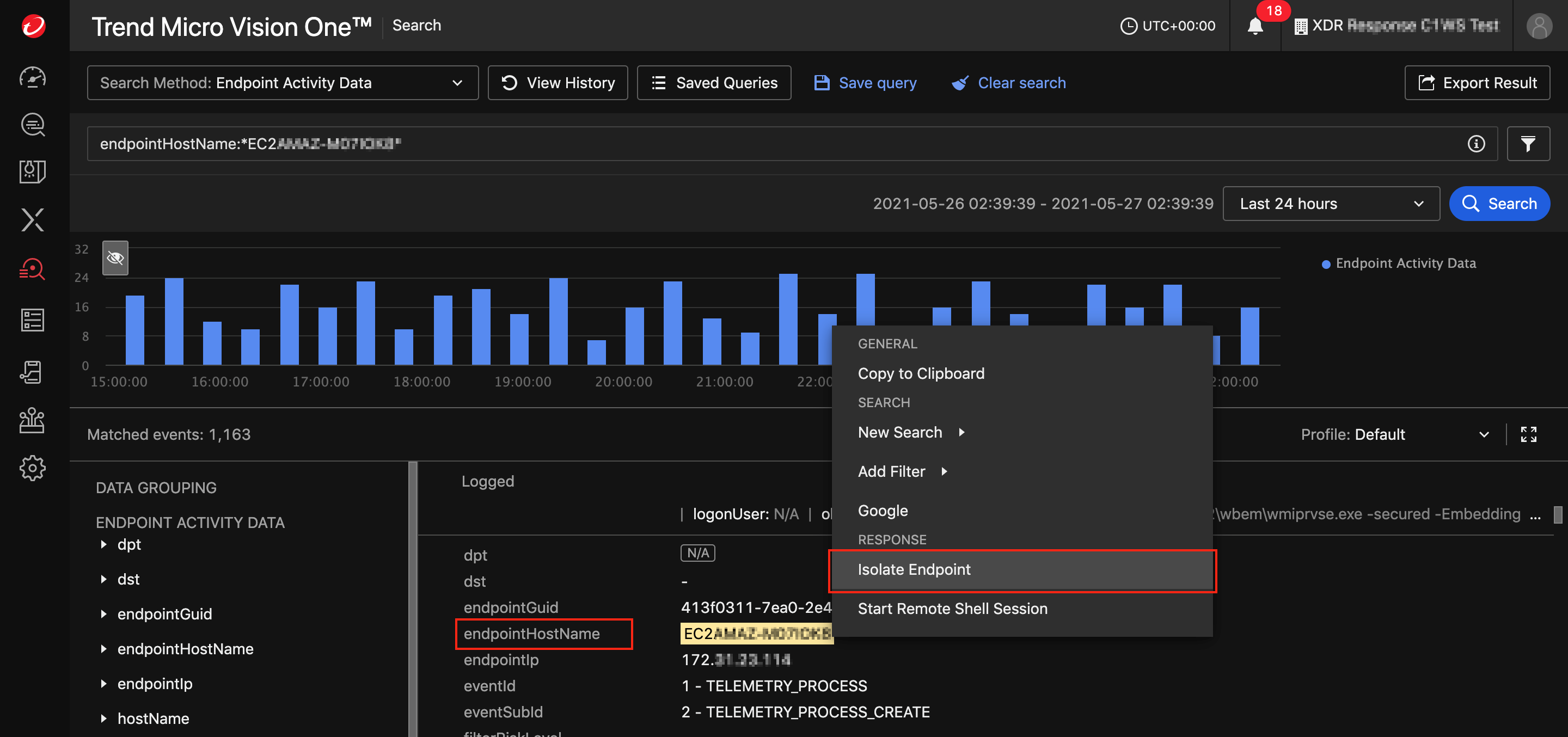
The Isolate Endpoint Task window appears.
From the Trend Vision One Workbench (under XDR  ):
):
Right-click on the server icon ![]() for the endpoint you want to isolate and select Isolate Endpoint.
for the endpoint you want to isolate and select Isolate Endpoint.
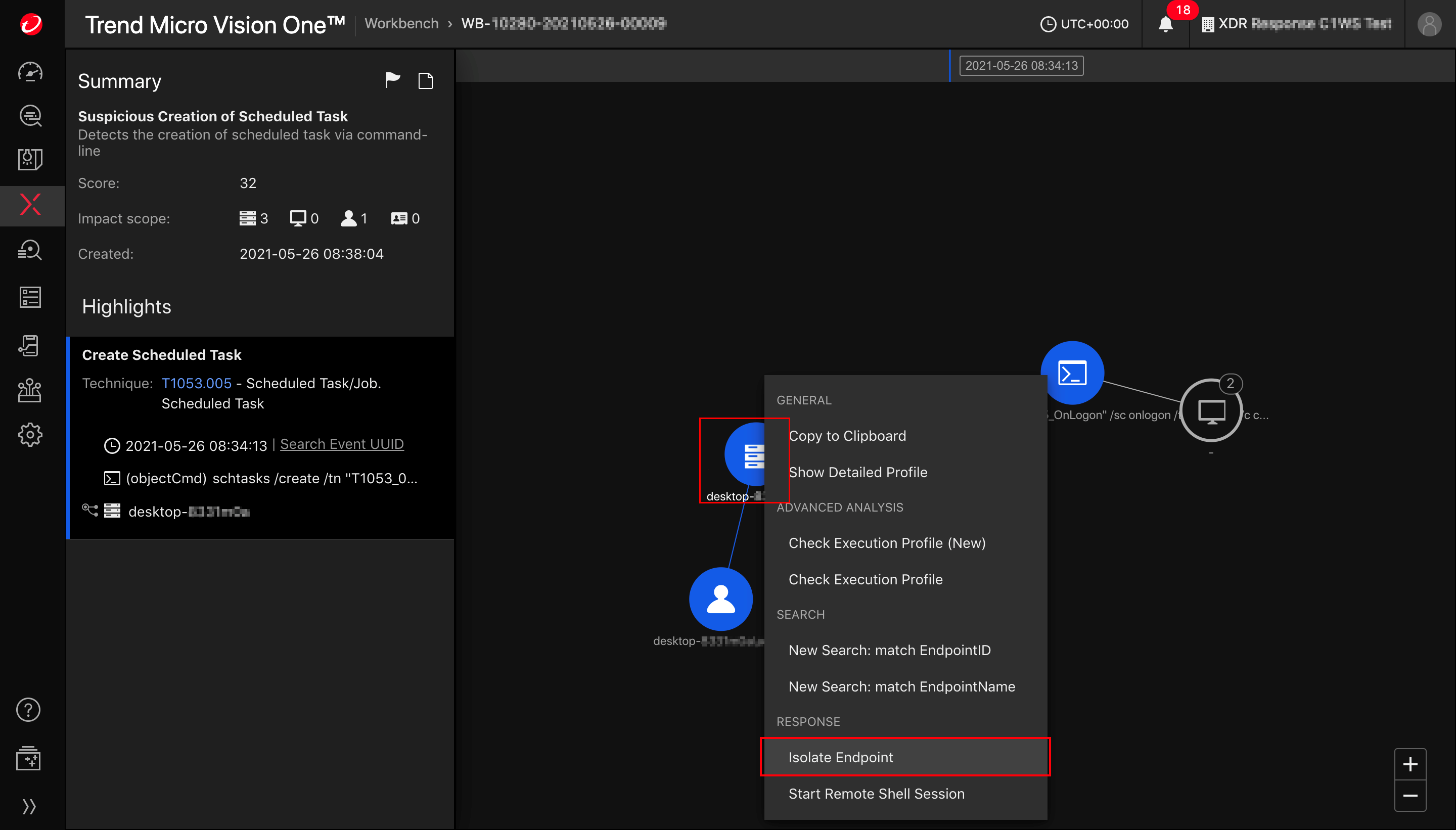
The Isolate Endpoint Task window appears.
From the Trend Vision One Observed Attack Techniques tab (under XDR  ):
):
Right-click on the "Associated endpoint" that you want to isolate and select Isolate Endpoint.
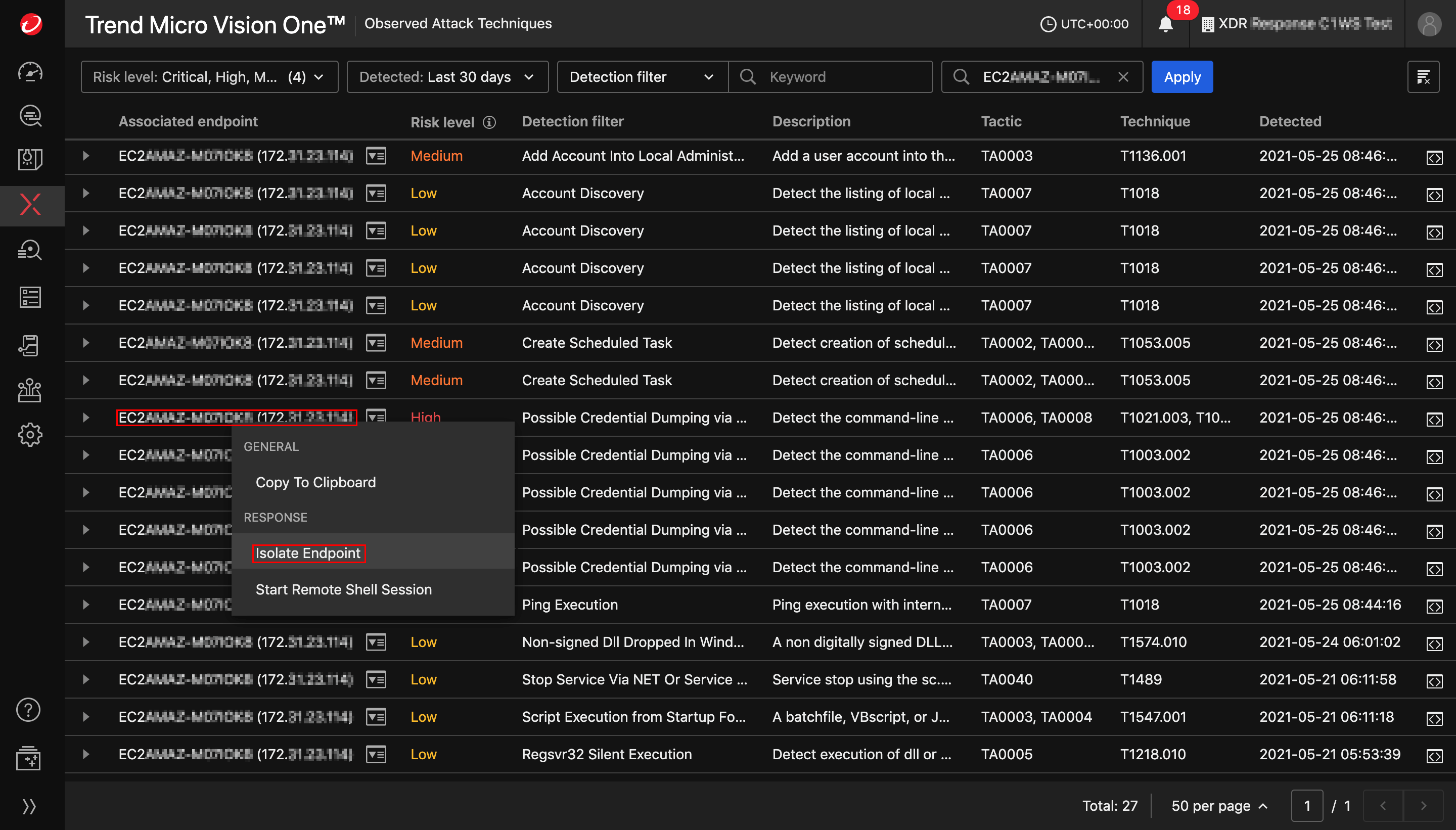
The Isolate Endpoint Task window appears.
Create an Isolate Endpoint Task
From the Isolate Endpoint Task window:
- Optionally, enter a description for the task.
- Select Create to start the task.
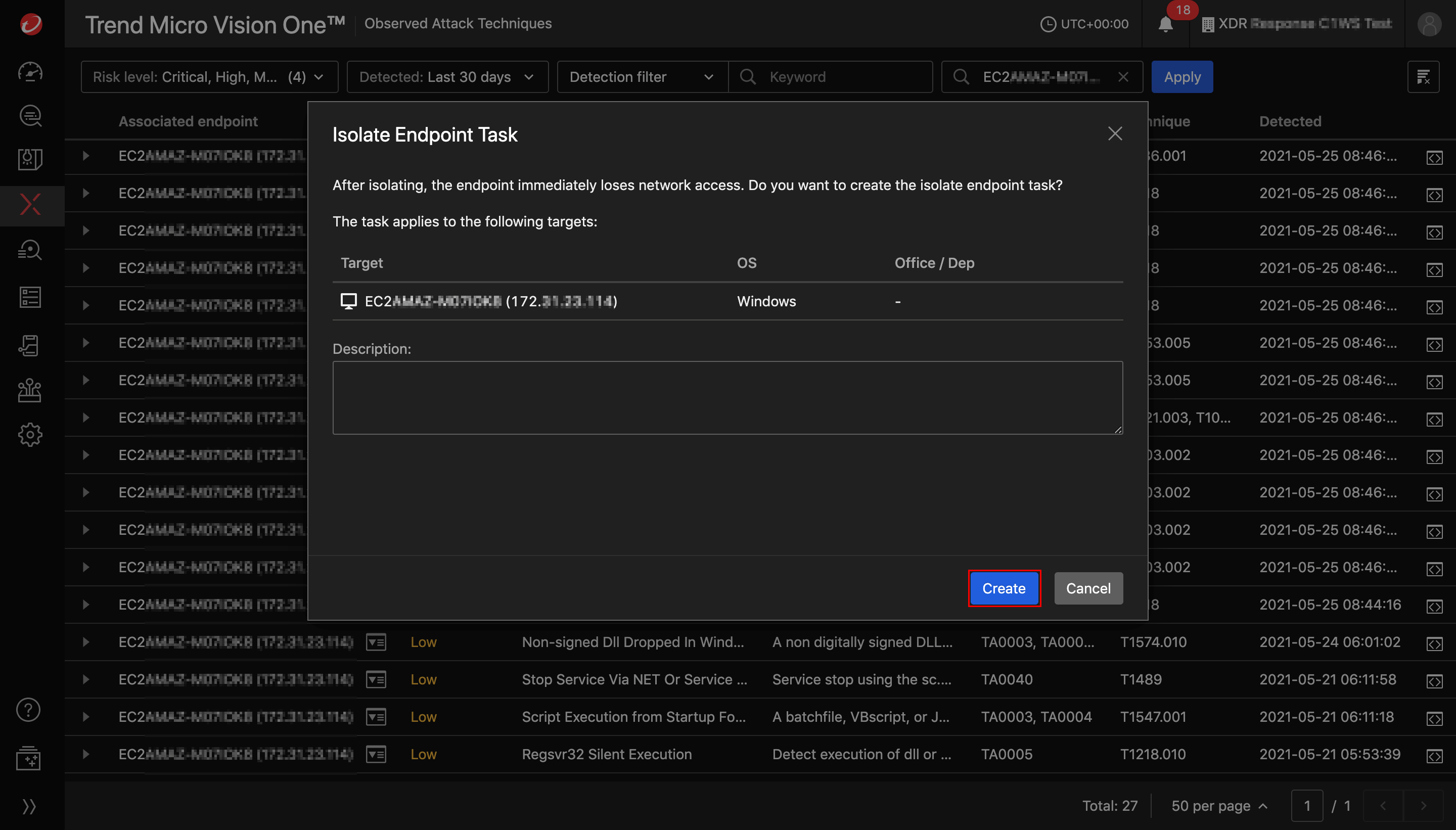
Monitor task status
You can monitor tasks from Response Management ![]() .
.
Task status indicates whether or not the managing server was able to successfully receive and execute a command. If the command target is a Security Agent, the Task status does not necessarily indicate that the target Security Agent or object successfully executed the command.
Task statuses include:
 In progress: Trend Vision One sent the command to the managing server and is waiting for a response.
In progress: Trend Vision One sent the command to the managing server and is waiting for a response. Queued: The server queued the command due to a high volume of requests or because the Security Agent was offline.
Queued: The server queued the command due to a high volume of requests or because the Security Agent was offline. Successful: The managing server successfully received the command.
Successful: The managing server successfully received the command. Unsuccessful: An error or time-out occurred when attempting to send the command to the managing server.
Unsuccessful: An error or time-out occurred when attempting to send the command to the managing server.
You can locate tasks by using the Search field or selecting Isolate Endpoint from the Action list.
Restore connection to an endpoint
After resolving the security issues on an isolated endpoint, you can restore its network connectivity from Response Management ![]() .
.
Select the options button 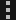 beside the endpoint and select Restore Connection.
beside the endpoint and select Restore Connection.
Troubleshoot common issues
To troubleshoot common issues triggering Network Isolation or Restore Connection, check the following settings in your Workload Security console:
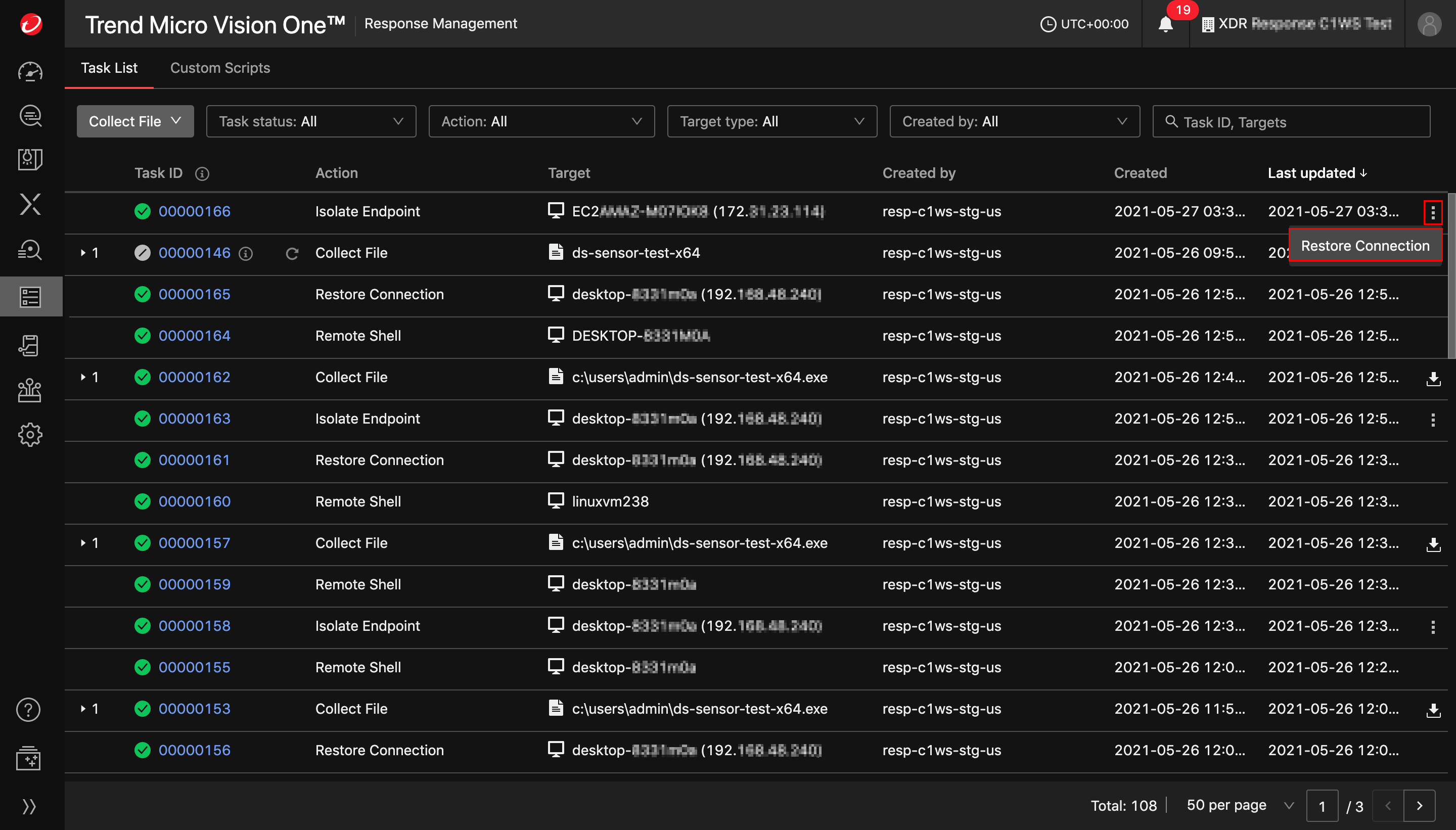
Trend Vision One settings
In the Trend Vision One (XDR) tab (Administration > System Settings > Trend Vision One (XDR)), make sure that:
- Enrollment status is Registered
- Forward security events to Trend Vision One has its checkbox selected
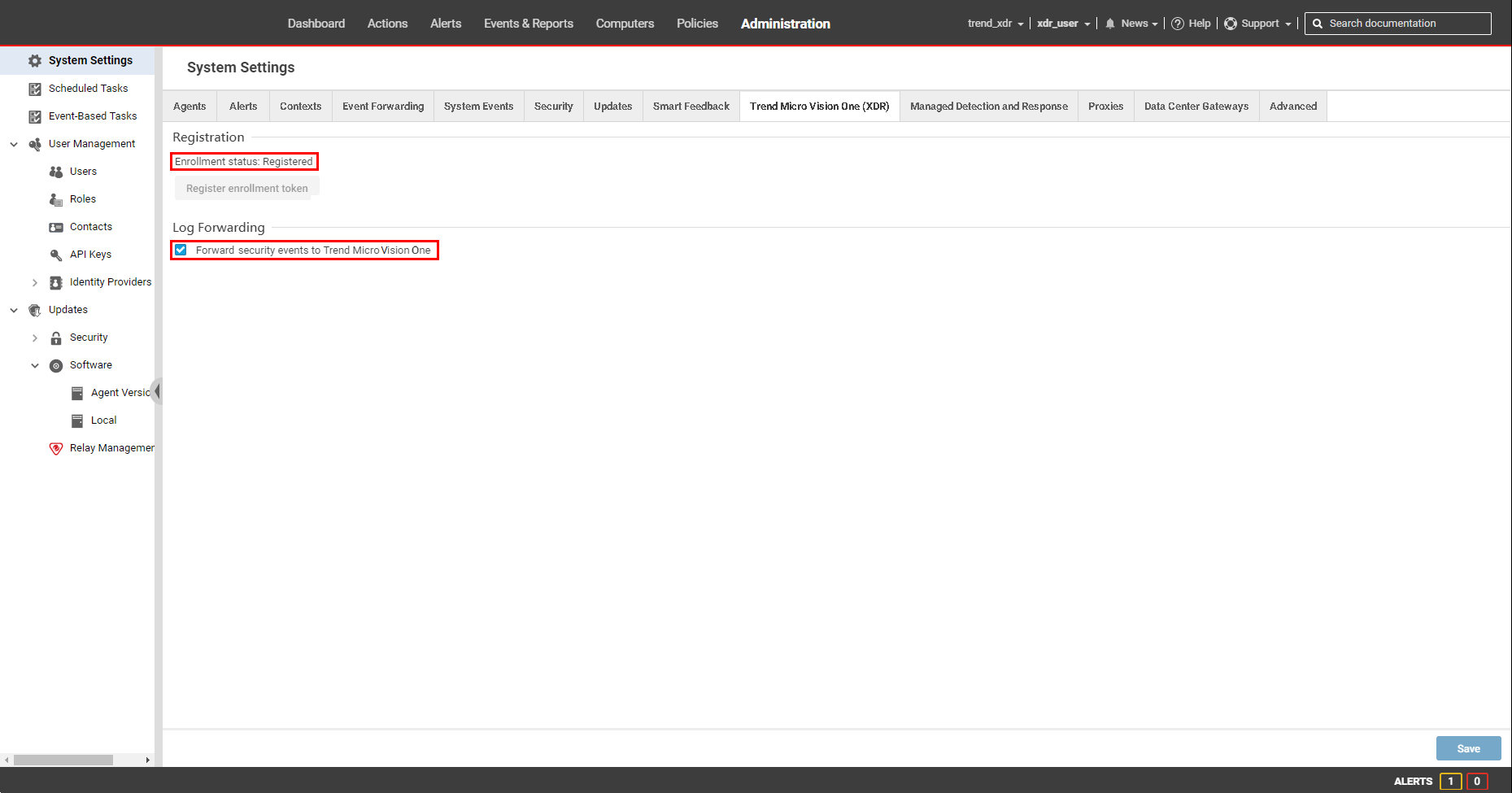
Security module settings for your computers
In the Activity Monitoring tab for your computers (Computers > (Right- or- double-click) Details > Activity Monitoring > General), make sure Configuration is set to On or Inherited (On).
You can also enable Activity Monitoring for computers by enabling it in the policy assigned to them. From the Policies tab, double-click the policy for which you want to enable Activity Monitoring. Go to the Activity Monitoring > General and make sure that Activity Monitoring State is set to On.
If you have checked the requirements and troubleshoot common issues sections, but are still experiencing problems, contact support.