Topics on this page
Template Scanner Github App
Template Scanner Github App scans your infrastructure-as-code templates and evaluates them against the best security practices. You can select repositories within your organization to automatically scan a pull request you open or update it in your selected Github repositories.
We currently do not support the Github Enterprise organizations.
- How to install the Template Scanner Github App?
- How to configure what gets scanned?
- Available configuration
- Special characters for matching a path portion:
- Note on the use of dots (.)
- Examples:
- Supported infrastructure as code
- CloudFormation YAML and JSON
- Terraform
- How to trigger a scan?
How to install the Template Scanner Github App?
Please follow the steps on Getting started with GitHub Source Accounts to install the Github App.
How to configure what gets scanned?
By default, Template Scanner Github App scans CloudFormation templates at the root of the repository, e.g. cloudformation.yml, cloudformation.json, template.yml and terraform ".tf" files at any level in the repository.
To configure and override what gets scanned:
1. Create a directory called .template-security in the root of the repository.
2. Add a config.json file in .template-security/ with your configurations.
Example:
{
"frameworks": {
"terraform": { "templateFilesPattern": "**/*(*.tf|*.tfvars)" },
"cloudformation": { "templateFilesPattern": "**/*(*.yml)" }
}
}Available configuration
frameworks: (object) contains the frameworks you would like to scan as keys. Supported values "terraform" | "cloudformation"templateFilesPattern: (string) use a file pattern to match files and directories.
Special characters for matching a path portion:
*Matches 0 or more characters in a single path portion?Matches 1 character[...]Matches a range of characters, similar to a RegExp range If the first character of the range is!or^then it matches any character not in the range.!(pattern|pattern|pattern)Matches anything that does not match any of the pattern.?(pattern|pattern|pattern)Matches zero or one occurrence of the pattern.+(pattern|pattern|pattern)Matches one or more occurrences of the pattern.*(a|b|c)Matches zero or more occurrences of the pattern@(pattern|pat*|pat?erN)Matches exactly one of the pattern**If a "globstar" is alone in a path portion, then it matches zero or more directories and subdirectories. Note that this does not crawl symlinked directories.
Note on the use of dots (.)
If a file or directory path portion has a . as the first character,
then it will not match any glob pattern unless that pattern's
corresponding path part also has a . as its first character.
For example, the pattern a/.*/c would match the file at a/.b/c.
However the pattern a/*/c would not, because * does not start with
a dot character.
Examples:
- `*(*.tf)` Match only files ending with `.tf`
- `**/*(*.tf|*.tfvars)` Starting from the top directory, match files ending with `.tf` or `.tfvars`
- `*(*.tf|*.tfvars)` Match files ending with `.tf` or `.tfvars` in the root directory only
Supported infrastructure as code
CloudFormation YAML and JSON
Supported resource types:
- APIGateway RestApi
- AutoScaling Group
- AutoScaling Launch Configuration
- CloudFormation Stack
- CloudTrail Trail
- DynamoDb Table
- EC2 Instance
- EC2 NatGateway
- EC2 Network Acl
- EC2 Network Interface
- EC2 Route Table
- EC2 Security Group
- EC2 Subnet
- EC2 Volume
- EC2 VPC
- EC2 VPC Endpoint
- EFS File System
- Elastic Load Balancer v2
- ElasticCache
- Elasticsearch Domain
- ELB Classic Load Balancer
- EMR Cluster
- IAM Group
- IAM Managed Policy
- IAM Role
- Kinesis Stream
- KMS Key
- Lambda Function
- RDS Cluster
- RDS Instance
- Redshift Cluster
- S3 Bucket
- SNS Topic
- SQS Queue
- Workspaces
Terraform
Supported resource types:
- DynamoDB
- EC2 Instance
- Elastic Load Balancer v2
- S3 Bucket
- RDS Cluster
- RDS Instance
- SNS Topic
- SQS Queue
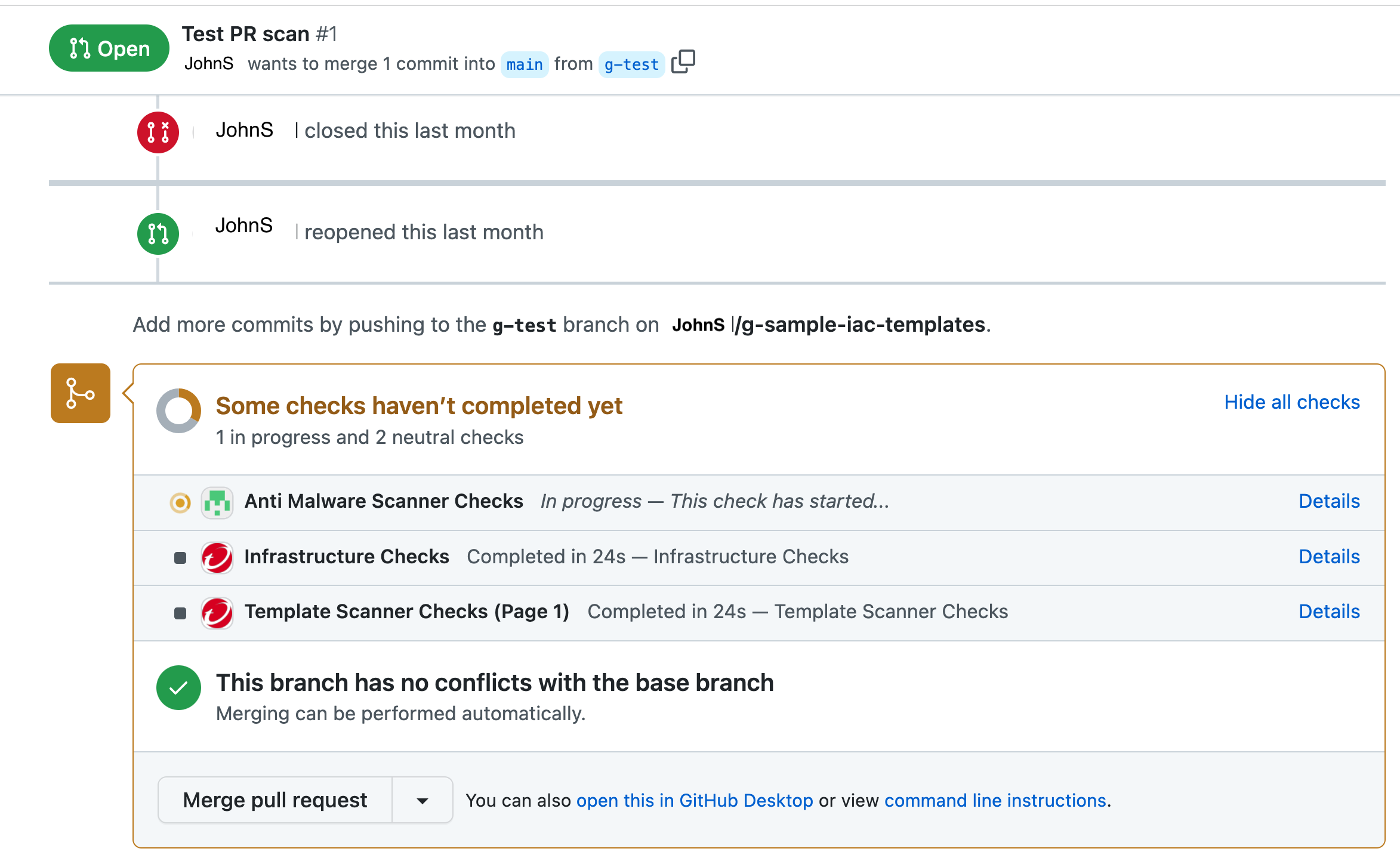
How to trigger a scan?
To trigger a scan:
- Create a pull request in Github for the repository where you installed the Template Scanner Github App. You should be able to view the status of the scan at the bottom of your pull request in Github.
- Click on Details to view the findings generated by the scan.