Topics on this page
Set Up SSO For Your Organisation
Please see Cloud One User Management if you’re accessing Conformity through the Cloud One console. This documentation is relevant only to Conformity standalone customers.
User Access
| User Role | Can Access |
|---|---|
| Administrator | |
| Power User | |
| Custom - Full Access | |
| Read Only | |
| Custom - Read Only |
Single sign-on (SSO) enables you to securely authenticate and access Trend Micro Cloud One™ – Conformity along with multiple applications and websites by logging in only once—with just one set of credentials. Conformity supports SAML 2.0 SSO standard.
Enabling SSO for Conformity is a two-step process explained below:
Contents
Step 1: Send a domain validation request
To enable you to set up SSO for your organization, we first need to validate your domain.
Decide upon the primary domain for your organization and send an email to support@cloudconformity.com or create a support ticket titled ‘SSO request - Domain validation’.
Please ensure that your domain name:
- Is owned by your organization
- Must not be a free public domain eg: gmail.com, rediffmail.com, and hotmail.com
- Must be in the correct format eg: abc.abc.com
- Must be a top-level-domain, according to the Mozilla public suffix list, or second-level-domain eg: .com, .co.uk
Once we validate your domain and activate SSO settings, we’ll notify you with a confirmation email.
If you need support for multiple email domains managed within the same IDP instance, please let our support team know in the ticket and we can assist.
Step 2: Configure SSO settings
On receiving the domain validation confirmation, sign in to Conformity and go to Administration > SSO to configure the following settings and activate SSO:
- Organisation domain: your validated organization domain name is populated by default. To update the domain name, you will need to go through the validation process again by creating a support ticket or sending an email.
-
Identify provider: select an Identity Provider for your organization from the drop-down list. Ensure that all users in your organization use the same SSO provider for accessing Conformity. We currently support Okta, ADFS, Microsoft Entra ID (Requires Premium Azure subscription), Centrify, Keycloak, and OneLogin.
If your Identity Provider is not listed and it supports SAML 2.0, contact support to set it up for you.
We support any SAML 2.0 compliant identity provider in SP-init sign-on (authentication starts on CC SSO page: https://www.cloudconformity.com/identity/saml-sign-in.html). We also support IdP-init sign-on (authentication starts from the Identity Provider’s user dashboard) if the identity provider supports the "Default Relay State" value.- In addition to the options available from the drop-down list, we support the following Identity Providers out-of-the-box with LTS support: 1. Microsoft ADFS (All versions that Microsoft still supports) 2. AWS SSO 3. OneLogin 4. Microsoft Entra ID 5. OpenAM 6. IBM Security Access Manager 7. PingFed - For more information, refer to our integration guides for [Okta](okta-saml-sso-integration-set-up.md) and [ADFS](adfs-saml-sso-integration-set-up.md) or email [SSO@cloudconformity.com](mailto:SSO@cloudconformity.com) to receive instructions on integrating Conformity with Microsoft Entra ID, Centrify, Keycloak, and OneLogin.<br /> -
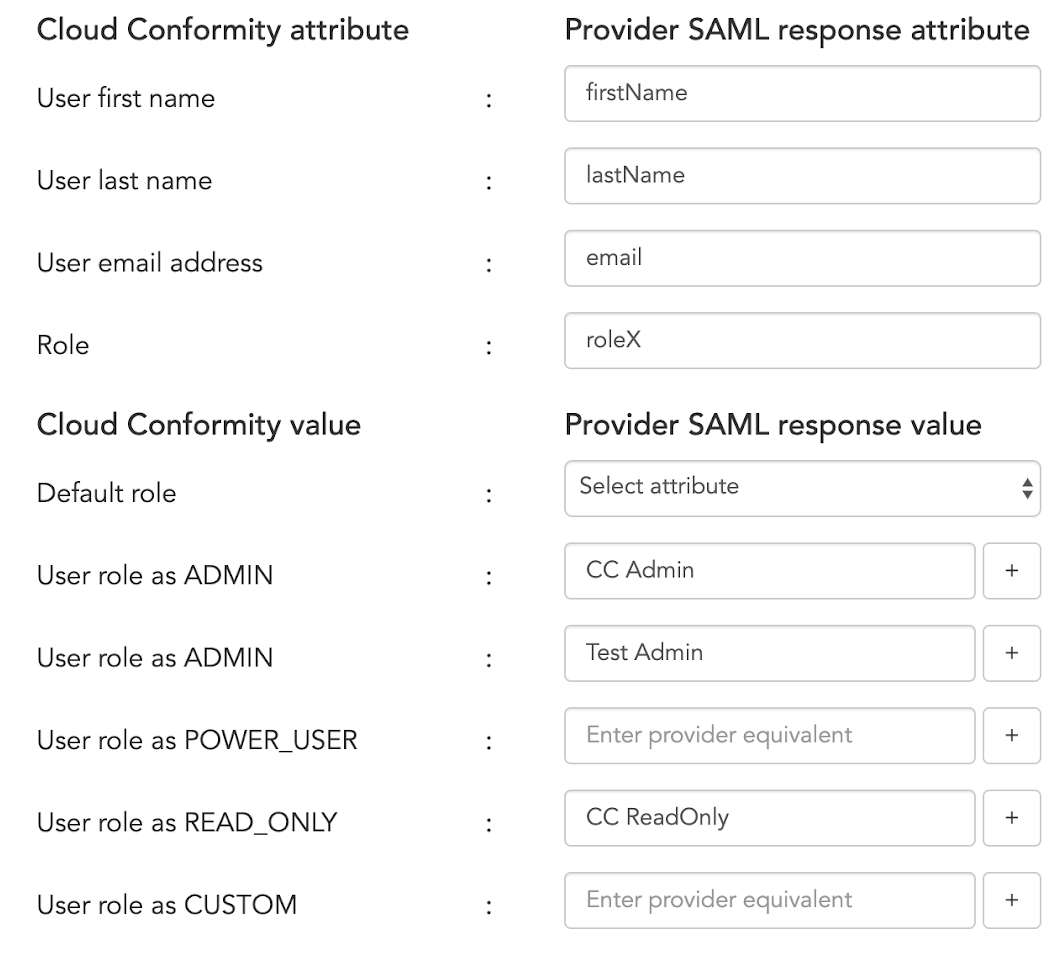
Mappings: map your identity provider’s SAML response attributes and values to Conformity. Make sure that you have integrated Conformity with the selected identity provider to be able to get SAML response attributes and values.
- Cloud Conformity attribute - the Conformity user attribute to be matched with the selected identity provider’s user attribute.
- Provider SAML response attribute - enter the selected identity provider’s equivalent value to match with Conformity attributes. For example, for Cloud Conformity attribute > User first name, enter the attribute used for the selected identity provider user’s first name.
- Cloud Conformity value: the cloud conformity user role value to be matched with Provider SAML response Role value.
- Provider SAML response value: the provider’s SAML response role value equivalent of the Cloud Conformity value. For example, for Conformity value > User role as READ_ONLY, enter the attribute used for the identity provider’s role with read-only access. For more information on Conformity user roles, see: Roles and Permissions.
- Default Role: select an attribute from the drop-down list to assign a default Conformity role to all SSO users who don’t have roles assigned by their identity provider.
It is mandatory to map Cloud Conformity attribute > User role as ADMIN to ensure that you retain administrative access to your organization. You can either select Admin as the Default Role or map to SAML provider Role value.
-
Select a SAML response signature/encryption order:
- Sign then encrypt - for ADFS identity providers
- Encrypt then sign - for all non-ADFS identity providers
-
Select a SAML logout request encryption algorithm:
- SHA512 - for all non-ADFS identity providers
- SHA256 - for ADFS identity providers
-
Copy and paste the Identity provider metadata. Please refer to your selected SAML provider integration guide on how to get metadata or send an email requesting the integration steps.
-
Click on Test run settings to test your authorization and authentication settings.
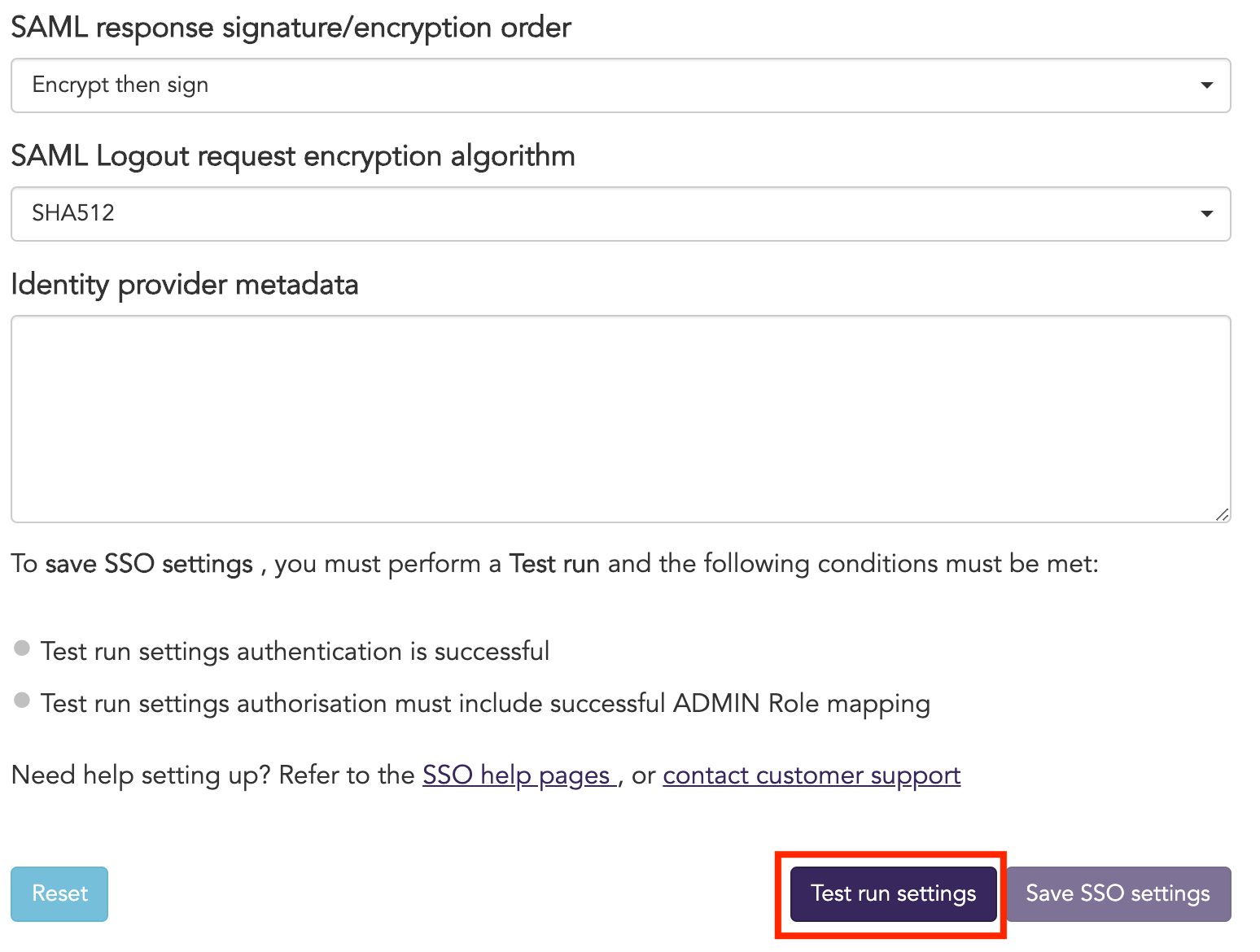
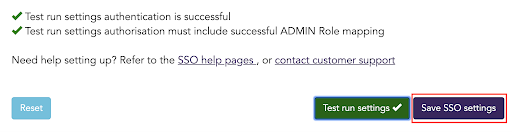
Every time you update SSO settings, you will need to perform a test run before you save the new settings. The option to save SSO settings will be disabled until your test run is successful. Once your test run is successful the Save SSO settings button becomes clickable.
-
Click on Save SSO settings.
-
Click on Yes to confirm the settings. On successful activation, a notification is displayed at the top of the SSO Settings page.
- Click on the Perform a sign in via Identity provider link from the notification to sign in to Cloud Conformity using SSO.
Once you have set up SSO, we recommend that you disable your local authentication by raising a support ticket.
FAQs
Q: Do you support OAuth authentication?
A: No. If you have a specific use-case where SAML 2.0 is not relevant, contact the Customer Success team and they will provide guidance or relay your feature request.
Q: Do you provide standard service-provider metadata?
A: Yes. https://us-west-2.cloudconformity.com/v1/sso/saml/metadata.xml
Q: Which nameid formats do you support?
A: Preferably urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress, although we can work with urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified as long as the value is either email address, or otherwise unique, and email address is sent as another unique attribute.
Q: Which SAML attributes do you support?
A: Apart from the email address that is preferably the nameid, Conformity can map first name, last name, and user role from any SAML attribute.
Q: Do you need SAML response/assertions to be encrypted/signed?
A: The response has to be signed, but encryption is optional.
Q: Can we use multiple identity providers?
A: Yes. However, keep in mind that users within the same organization using different identity providers are not fully isolated and their personally identifiable information will be accessible to other users.
Q: Can we use local Conformity username/passwords alongside SSO?
A: Yes. However, we recommend disabling local authentication after SSO setup. This can be requested via the customer support portal.
Q: What access level do SSO users get?
A: SSO users can get one of the following roles in Conformity:
- Admin: Full access to the organisation, and all accounts
- Power user: Full access to all accounts
- Read-only: Read-only access to all accounts
- Custom: By default has no access, can be granted account-level permissions (full, read-only, none) on Conformity user management by an Admin.
Depending on your identity provider, you can configure it to send a group membership or role attribute with values that would map to the roles mentioned earlier.
Q: I have my own internal identity management, how would authorization work with SSO?
A: Cloud Conformity will accept the roles your users are signing in to authorize access, i.e. if a user signs in as an Admin, they will be treated as an Admin.
Q: What if we have groups of users that require access to separate sets of accounts?
A: You can have one Admin group to manage user permissions and add accounts and map everyone else to the Custom role. You can manage account-level permissions on Conformity user management.
Q: What if we have a lot of users with custom permissions? It's not efficient to wait for all of them to sign in before we can manage their permissions.
A: If you have many users with custom permissions, first add all of your accounts, then request bulk user import in CSV format via the customer support portal.
Q: How does user provisioning work when SSO is enabled?
A: Conformity supports Just in Time user provisioning. Any successful SSO authentication triggers Conformity to update the existing user with the provided first name, last name, and role; or create a new user with the provided attributes.
Q: How can I revoke an SSO user in Conformity?
A: If your SSO configurations allow local sign-on (username/password), you can revoke users as an Admin from Conformity UI. If a user is fully managed by the Identity Provider, you will need to raise a support ticket.
Q: Do you support break-glass credentials in case our identity provider is not working or SSO configuration requires an update?
A: Yes. You can mention that you would like to keep the user credentials when you request local credentials removal via the customer support portal.