Topics on this page
Review your cloud environment
Before you deploy the Network Security endpoints, review your infrastructure and analyze the specific security outcomes and requirements that you want Network Security to meet. Network Security can protect many different environment configurations and deployments.
Hosted infrastructure deployments are currently supported in the following AWS regions:
- us-west-1, us-west-2
- us-east-1, us-east-2
- sa-east-1
- ap-south-1
- ap-southeast-1, ap-southeast-2
- ap-northeast-1, ap-northeast-2, ap-northeast-3
- eu-central-1
- eu-north-1
- eu-west-1, eu-west-2, eu-west-3
- ca-central-1
Below are a few examples of different environment configurations with public facing assets to help you configure Network Security endpoint deployment and routing.
- Environments that use an Application Load Balancer (ALB)
- Environments with routing at the Edge
- Environments that use a Transit Gateway
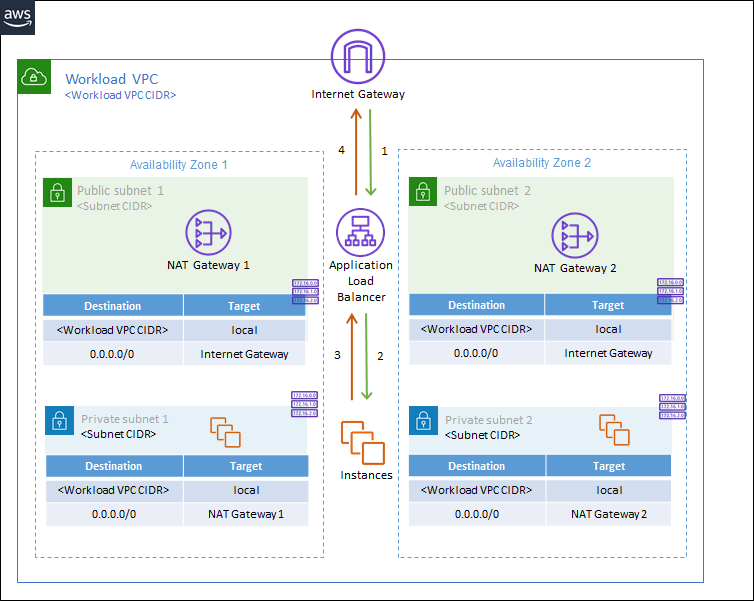
Environments that use an Application Load Balancer (ALB)
This configuration is best suited for cloud environments that require enhanced protection for ALB targets in a single VPC. ALBs enable TLS termination for encrypted IPv4 traffic to help with TLS inspection as well as more specific routing so that traffic can be distributed to multiple targets and AZs in your environment. Learn more about how Application Load Balancers are supported in AWS.
These type of environments typically include "Workload" VPCs, which are VPCs with public facing assets, as well as an Internet Gateway. Each AZ within the VPC also includes a NAT gateway and public and private subnets with a default route table for each.
In this deployment type, traffic flows from the Internet Gateway to the Workload VPC using the ALB and the NAT gateways. The ALB then distributes the traffic to the resources in the various Workload VPC AZs. After the Network Security endpoints are deployed, this traffic is diverted to Network Security for inspection after the traffic passes through the ALB.
Below is a scaled-down example of what this type of environment might look like before Network Security endpoints are deployed. Green represents inbound traffic and orange represents outbound traffic.
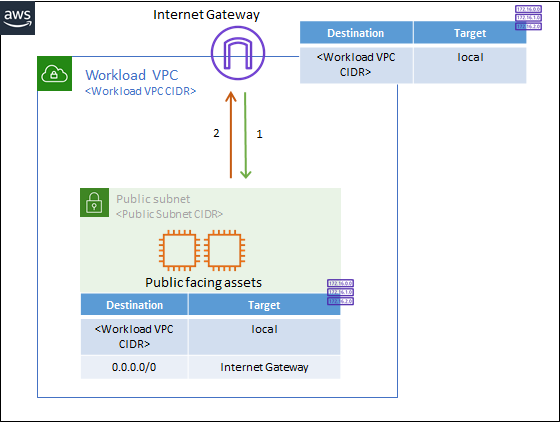
Environments with routing at the Edge
This configuration is best suited for cloud environments that include public facing assets, which need protection from inbound internet traffic, but that do not use an ALB. These environments often require protection for public assets in a single VPC. These types of environments typically include "Workload" VPCs, which are VPCs with public facing assets, as well as an Internet Gateway and a public subnet with a route table.
In this deployment type, traffic flows into the Workload VPC from the Internet Gateway to your public facing assets. After the Network Security endpoints are deployed, this inbound traffic is diverted to Network Security for inspection before reaching your public assets.
Below is a scaled-down example of what this type of environment might look like before Network Security endpoints are deployed. Green represents inbound traffic and orange represents outbound traffic.
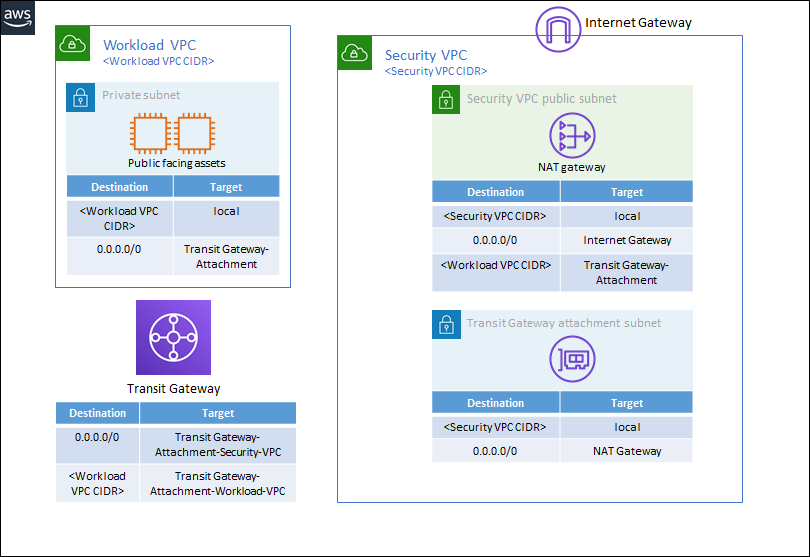
Environments that use a Transit Gateway
This configuration is best suited for cloud environments with a centralized architecture that use Transit Gateways to send traffic between different VPCs. These environments often require protection of assets in multiple VPCs connected with a Transit Gateway. AWS Transit Gateways are often used to support 'hub-and-spoke' topologies. Learn more about AWS Transit Gateways.
In this deployment type, traffic can flow from Workload VPCs, which contain public facing assets, to a centralized, shared services VPC, called the Security VPC in this example. After the Network Security endpoints are deployed, traffic is diverted to Network Security for inspection after the traffic passes through the Security VPC.
Below is a scaled-down example of what this type of environment might look like before Network Security endpoints are deployed.
Before you deploy Network Security endpoints, make note of the following items in your cloud environment:
- VPC ID: Identify the VPC in your environment that needs protection. This is the VPC where Network Security endpoints should be deployed. For instance, if you use a Transit Gateway, you would deploy the Network Security endpoints in the centralized VPC, shown as the "Security VPC" in the example above.
- Availability Zones (AZs): Identify the AZs in the selected VPC. A Network Security endpoint should be deployed in each AZ of the protected VPC.
- Subnet IDs or /28 CIDR ranges: Each Network Security endpoint requires a dedicated subnet. We recommend that you create this subnet in each AZ where Network Security endpoints will be deployed. Alternatively, you can enter an available CIDR range (we recommend using a /28 CIDR) for Network Security to create these dedicated subnets during endpoint deployment.
After you review your environment, create the Network Security endpoints.