Topics on this page
Troubleshooting by bypassing inspection
If you encounter network issues that disrupt inspection in your cloud environment, you can rule out Network Security as the source of these issues by briefly bypassing inspection. To bypass inspection, you can use either an API command or manually modify the route table that sends traffic to your Network Security endpoints for inspection.
Use an API to bypass inspection
Use the following API to bypass inspection for a specific AWS account and region. Learn more about this API in the API reference documentation.
https://network.{region}.cloudone.trendmicro.com/api/nsaas/inspection-bypass
Request sample:
{
"accountId": "1234567890",
"action": "bypass",
"awsRegion": "us-west-2"
}
Manually bypass inspection
To manually bypass inspection, change your routes back to their original status. Ensure that all routes that target the Network Security endpoints are removed. Make these modifications for each Availability Zone (AZ) that has inspection enabled.
The scenarios below provide three specific approaches to modifying route tables based on deployment type. These steps may vary based on your specific configuration.
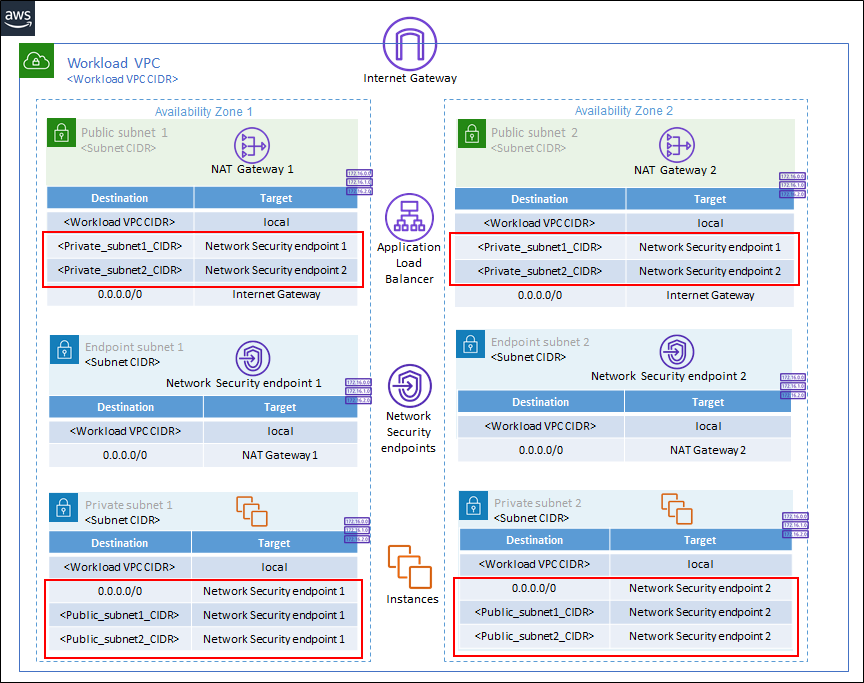
Environments with Application Load Balancers
If your deployment uses an AWS Application Load Balancer (ALB), examine and remove from all public and private subnet route tables any route that has a Network Security endpoint as the next hop, as shown below. Repeat for other AZs as needed.
Environments without Application Load Balancers
To modify routes for environments with public facing assets and an internet gateway, remove routes in two tables as shown below:
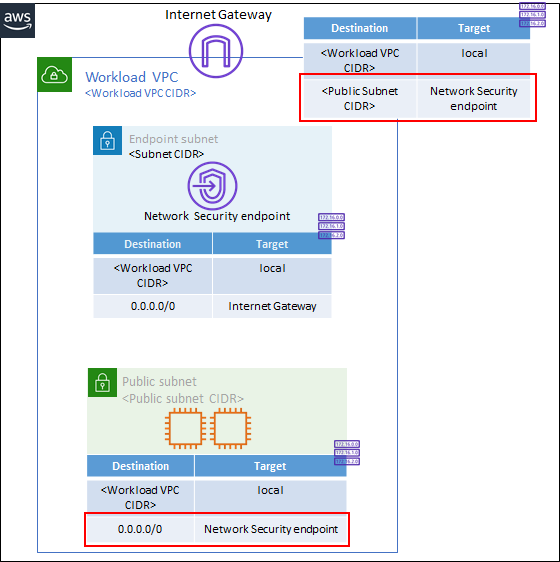
- In the main workload VPC route table, remove the route from Application Subnet CIDR to Network Security endpoint.
- In the Application Subnet route table, remove the route from "0.0.0.0/0" to Network Security endpoint.
- Repeat for other AZs as needed.
Environments with a Transit Gateway
To modify routes for environments with a centralized architecture that use Transit Gateways to send traffic between VPCs, remove the routes shown in the tables below to bypass traffic:
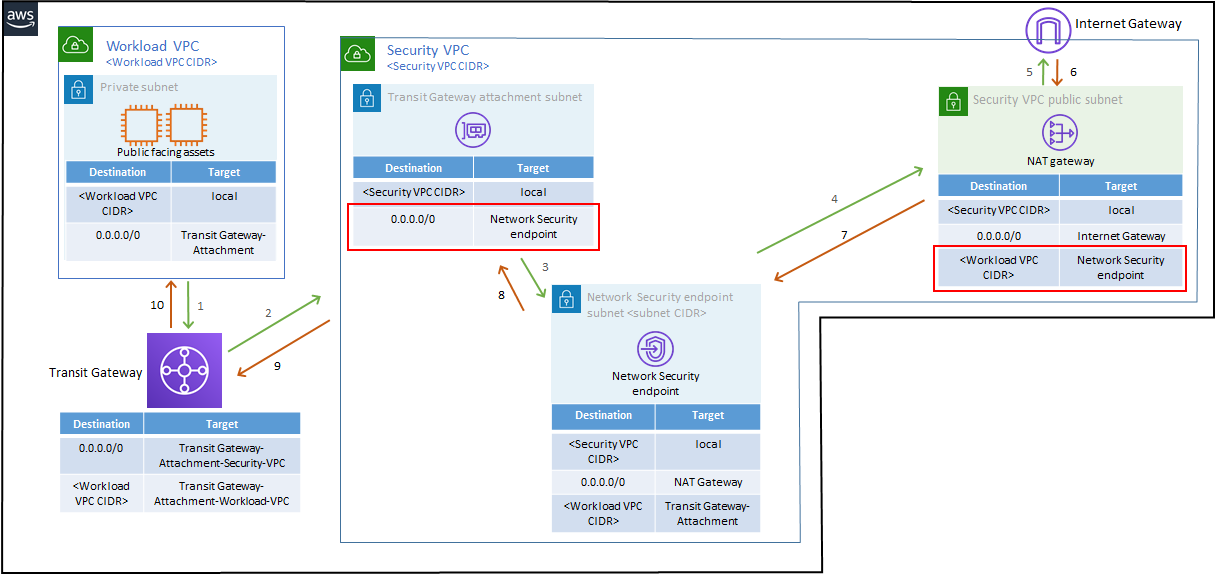
- In the Security VPC route table, remove the route from "0.0.0.0/0" to Network Security endpoint.
- In the Security VPC public subnet route table, remove the route from Workload VPC CIDR to the Network Security endpoint.
- Repeat for other AZs as needed.
Verification
After removing the routes to Network Security endpoints, verify that traffic is flowing as expected through the workload VPC and no bytes are inspected.
If your analysis indicates that Network Security is contributing to network issues, contact support.