Topics on this page
Deploy account scanner stacks
Account scanner stacks are designed for enterprise customers who want to deploy once and protect all their buckets within their account. They allow you to scan all of the S3 buckets in all of the regions of your account.
Architecture
The following architecture diagram illustrates the account scanner stacks and information flow.
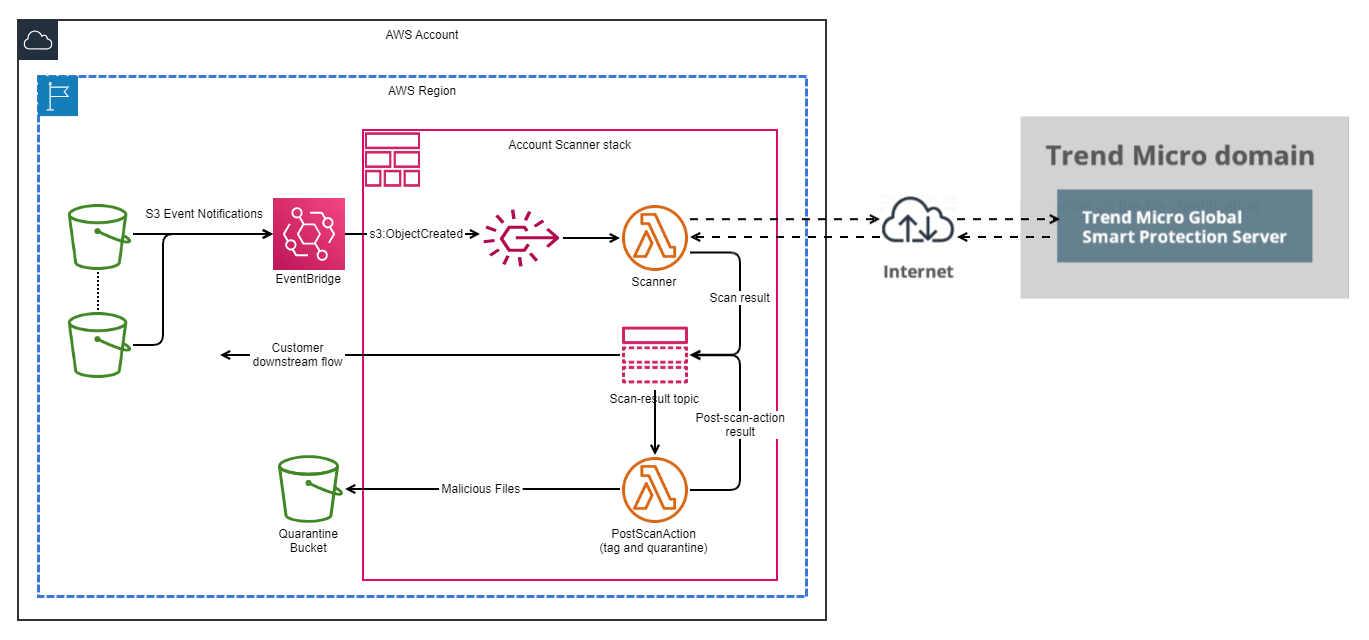
Currently, Trend Cloud One File Storage Security doesn't support deploying account scanner stacks through the UI. You must use the Cloud One File Storage Security APIs and the AWS CLI to deploy account scanner stacks:
- Enable Amazon EventBridge for your S3 buckets to trigger the account scanner stack to scan objects. Please refer to Enabling Amazon EventBridge for instructions.
- Create an API key.
- Call Describe Stack Deployment Template to obtain the template and parameters to deploy account scanner stacks.
Your response should resemble the following:
{ "templateURL": "https://file-storage-security.s3.amazonaws.com/latest/templates/FSS-Account-Scanner-Stack.template", "parameters": [ { "key": "CloudOneRegion", "value": "us-1" }, { "key": "ExternalID", "value": "123456789012" } ], "createStackURL": "https://us-east-1.console.aws.amazon.com/cloudformation/home?region=us-east-1#/stacks/quickcreate?templateUrl=https%3A%2F%2Ffile-storage-security.s3.amazonaws.com%2Flatest%2Ftemplates%2FFSS-Account-Scanner-Stack.template&stackName=Account-Scanner-TM-FileStorageSecurity¶m_ExternalID=123456789012¶m_CloudOneRegion=us-1" } - Create an account scanner stack using the AWS CLI:
aws cloudformation create-stack \ --stack-name ACCOUNT-SCANNER-STACK-NAME \ --region REGION \ --template-url TEMPLATE_URL \ --parameters \ ParameterKey=CloudOneRegion,ParameterValue=CLOUD-ONE-REGION \ ParameterKey=ExternalID,ParameterValue=EXTERNAL-ID \ ParameterKey=EnableCrossAccountScanning,ParameterValue=ENABLE-CROSS-ACCOUNT-SCANNING \ ParameterKey=KMSKeyARNForDLQSSE,ParameterValue=KMS-MASTER-KEY-ARN-FOR-DLQ \ ParameterKey=KMSKeyARNForTopicSSE,ParameterValue=KMS-MASTER-KEY-ARN-FOR-TOPIC \ ParameterKey=KMSKeyARNsForBucketSSE,ParameterValue=LIST-OF-KMS-MASTER-KEY-ARNS-FOR-BUCKETS \ ParameterKey=ReportObjectKey,ParameterValue=REPORT-OBJECT-KEY \ ParameterKey=ObjectCreatedEventFilter,ParameterValue=OBJECT-CREATED-EVENT-FILTER \ ParameterKey=ScanResultTagFormat,ParameterValue=SCAN-RESULT-TAG-FORMAT \ ParameterKey=QuarantineBucket,ParameterValue=QUARANTINE-BUCKET \ --capabilities CAPABILITY_NAMED_IAMWhere:
- ACCOUNT-SCANNER-STACK-NAME is replaced with the name of the stack. You can use any name. Example:
Account-Scanner-TM-FileStorageSecurity - REGION is replaced with the region where you want to install the stack. Choose one of the regions that contain that S3 buckets that you want to scan. For supported regions, see What regions are supported? Examples:
ap-east-2orus-west-2 - TEMPLATE_URL is replaced with the value of "templateURL" field in the response of the API in the previous step. Example:
https://file-storage-security.s3.amazonaws.com/latest/templates/FSS-Account-Scanner-Stack.template - CLOUD-ONE-REGION is replaced with the value of "value" field whose "key" field is "CloudOneRegion". It must be one of the supported Cloud One regions. Example:
us-1 - EXTERNAL-ID is replaced with the value of "value" field whose "key" field is "ExternalID". Example:
123456789012 - ENABLE-CROSS-ACCOUNT-SCANNING is replaced with true or false. Enable this if you want to scan S3 buckets in other AWS accounts. The AWS accounts should be in the same AWS organization.
- KMS-MASTER-KEY-ARN-FOR-DLQ is replaced with the ARN of your KMS master key which is used to encrypt messages in SQS queues in your scanner stack. Leave it blank if you haven't enabled SSE-KMS for SQS.
- KMS-MASTER-KEY-ARN-FOR-TOPIC is replaced with the ARN of your KMS master key which is used to encrypt messages published to the SNS topic in your scanner stack. Leave it blank if you haven't enabled SSE-KMS for SNS.
- LIST-OF-KMS-MASTER-KEY-ARNS-FOR-BUCKETS is replaced with the ARNs of your KMS master keys which are used to encrypt objects in your S3 buckets. It should be a comma-separated list. Leave it blank if you haven't enabled SSE-KMS for your S3 buckets. Example:
arn:aws:kms:::key/\,arn:aws:kms:::key/. Remember to escape commas with "\,". - REPORT-OBJECT-KEY is replaced with true or false. Enable this to report the object keys of the scanned objects to File Storage Security backend services. File Storage Security can then display the object keys of the malicious objects in the response of events API.
- OBJECT-CREATED-EVENT-FILTER is replaced with the JSON string which is part of the event pattern of the EventBridge rule in your scanner stack. The filter string will be used to filter the contents in "details" key of the S3 Object Created event. Please refer to the AWS official document about event patterns of Amazon EventBridge. Example:
{"bucket":{"name":[{"prefix": "example-"}]}} - SCAN-RESULT-TAG-FORMAT is replaced with one of the available formats of the tags:
Separated tags,Merged tagandNo tag. For more information, see View tags. - QUARANTINE-BUCKET is replaced with the name of the S3 bucket used to quarantine malicious objects. Leave this parameter blank to disable quarantining. The bucket region should be the same region as the account scanner stack.
- CAPABILITY_NAMED_IAM remains as is.
- ACCOUNT-SCANNER-STACK-NAME is replaced with the name of the stack. You can use any name. Example:
- Using the API, add the account scanner stack to File Storage Security.