Topics on this page
The Application Security interface
To help you to easily manage and monitor your security activity, Application Security provides a quick and easy to use interface.
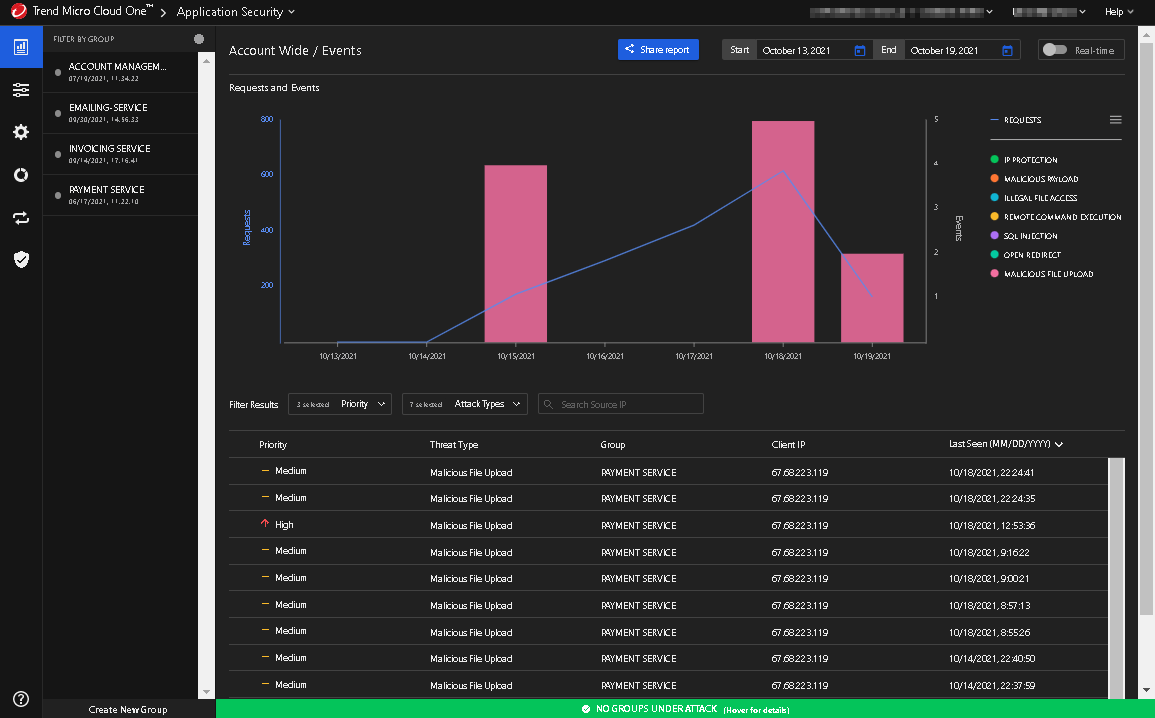
The interface is broken into two parts. The left navigation pane lists your groups and manages what is displayed on the right pane. The right pane is where you manage and monitor your groups and their security events.
Manage your groups
At the bottom of the left hand pane is the button where you create your groups. For more information please see Add a security group.
Once you have created your group, you can manage the group's configurations and policies:
-
The Group Configuration view allows you to manage a group's configurations. To access the Group Configuration view, click the Group Configuration icon,
 . For more information, see View and modify group configurations.
. For more information, see View and modify group configurations. -
The Group Policy view allows you to manage a group's policy settings. To access the Group Policy view, click the Group Policy icon,
 . For more information, see Configure a policy.
. For more information, see Configure a policy. -
The Integrations view allows you to integrate external apps to receive alerts from AppSec. It also lists the apps that already have been integrated. To access the Integrations view, click the Integrations icon,
 . For more information, see Integrations.
. For more information, see Integrations.
Monitor events and alerts
-
The Events view displays the number of requests and events that have occuured ove a specific time frame. An event is triggered when a security threat occurs and triggers a rule in your policy. By defaut, the Events window is shown in the right pane when you enter Application Security. To return to the Events window, click the Events icon,
 . For more information, see Manage events.
. For more information, see Manage events. -
The Usage view reports on the Application Security service usage, for example the number of invocations or instances protected. The usage is reported for the entire account, that is across all groups.To access the Usage view click the Usage icon,
 . For more information, see Track Usage.
. For more information, see Track Usage.
The Assessment view displays information derived from the serverless function configurations, the security controls and the policy configured in Application security. To access the Assessment view, click the Assessment icon, ![]() . For more information, see Manage the security assessment for serverless functions.
. For more information, see Manage the security assessment for serverless functions.