Topics on this page
Configure the security assessment for AWS
It's easy to set up and use the benefits of the Assessment view:
- Configure the access to the AWS account to retrieve the serverless asset information.
- Review the security assessment information reported and start improving on the security score.
Configure access to the AWS account
Application Security needs to get information from the AWS account in order to have visibility not only on the account's Lambda Functions, but also how these functions are configured. The security assessment is derived from the Lambda functions configuration, and the security controls and policy configured in Application Security.
To configure the access to the AWS account, follow these steps:
-
Click
 on the the left side panel to access the Application Security Assessment view:
on the the left side panel to access the Application Security Assessment view: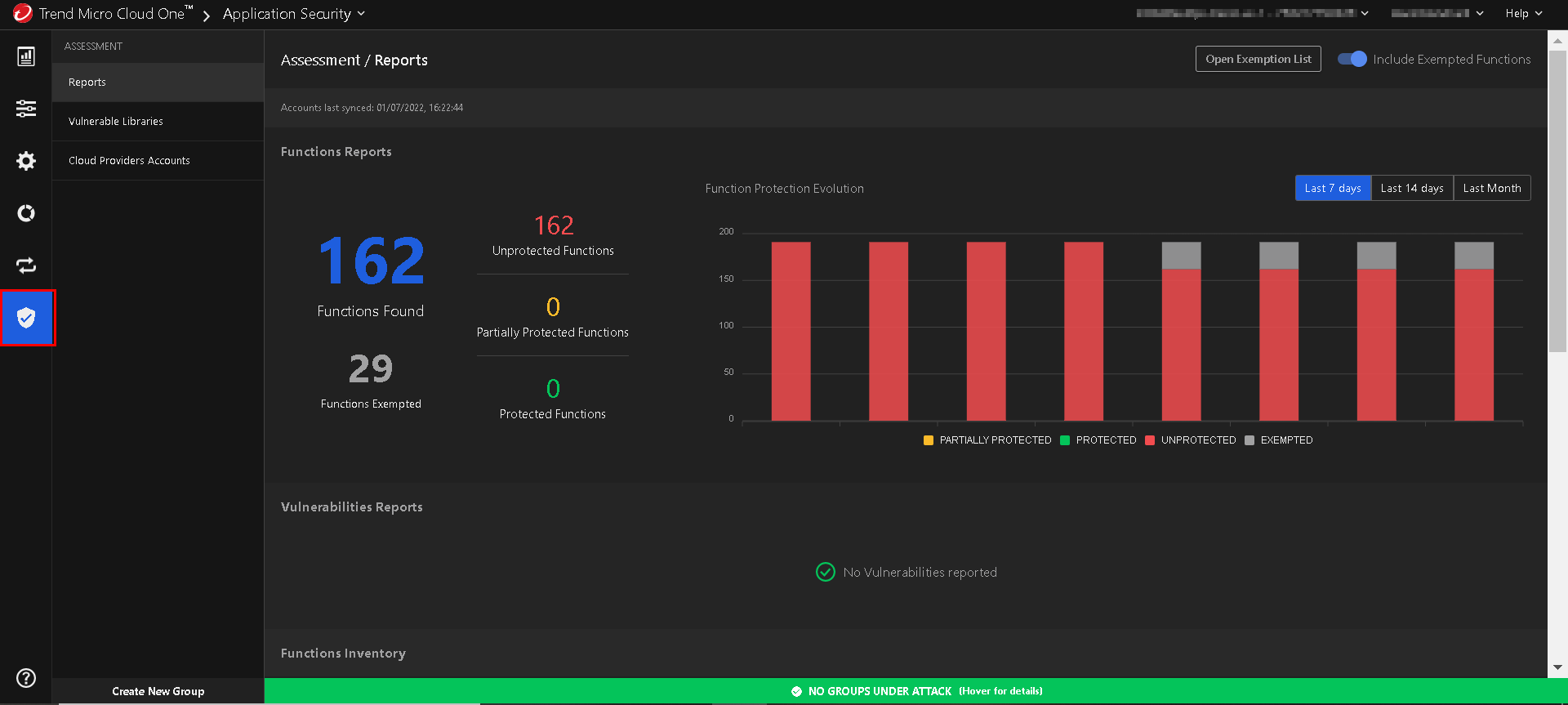
-
On a different tab in the same browser, log in to your AWS account.
Make sure the user that you are logging into the account with has the required privileges to create a AWS Cloud Formation stack.
-
In the Assessment view, select Cloud Providers Account.
-
From the top right side, select the Add Cloud Provider Account
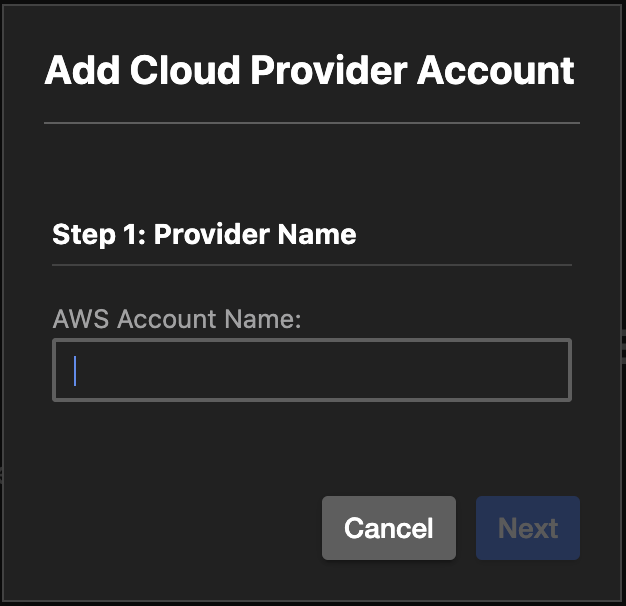
Selecting the Add Cloud Provider Account opens the dialog Going through the required configuration of the Cloud Formation stack provides the required access:
-
Provide a name for the provider account. That's the name that will be used to refer to the connection to the AWS account.
-
Select Next
-
Create the Cloud Formation stack in the AWS account:
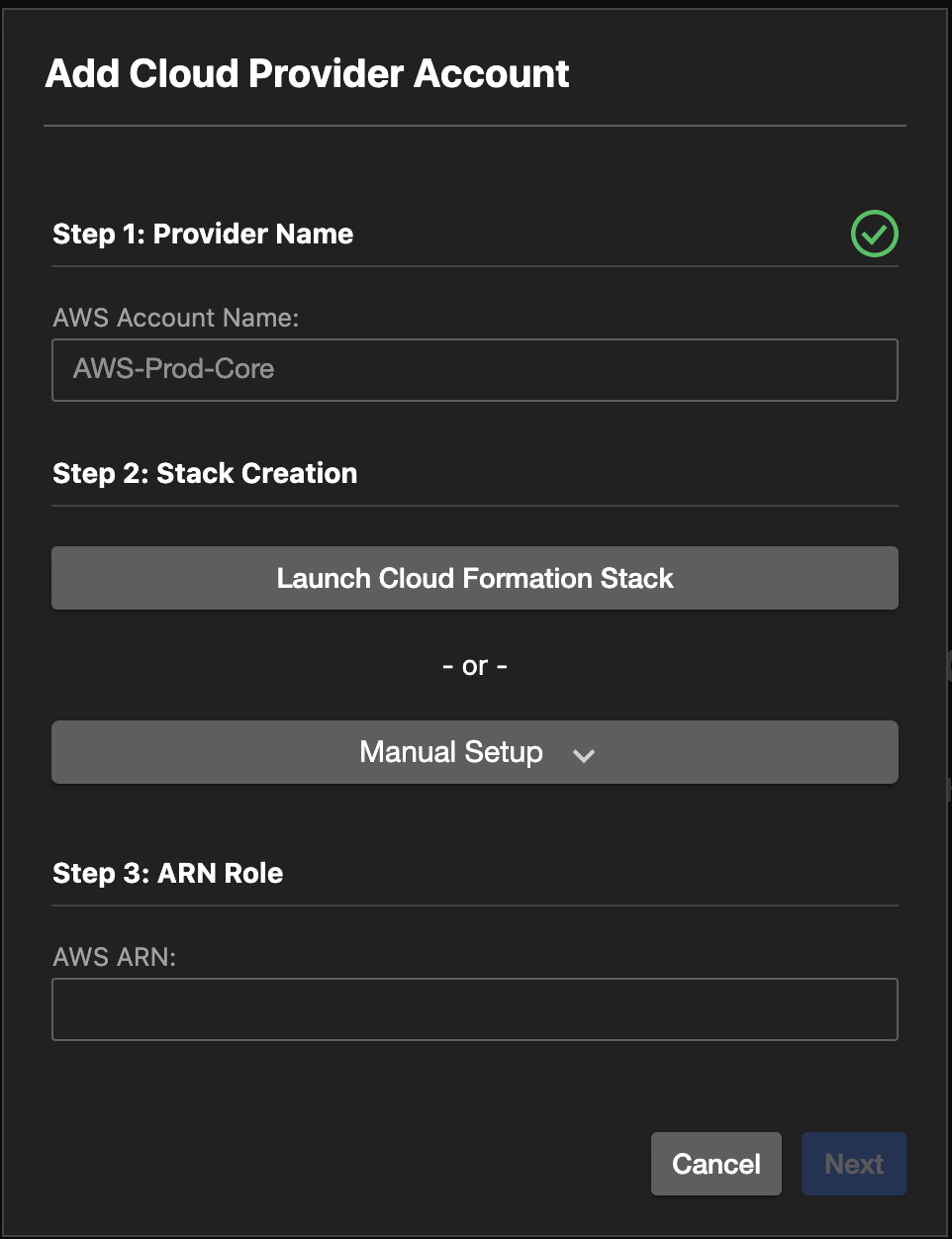
To create the stack in Cloud Formation, either:
-
Have Application Security automatically push the stack creation in the AWS account, from a template.
-
Manually create the Cloud Formation stack in AWS.
-
-
Configure the role ARN:
Once the Cloud Formation stack is created, go to the Outputs tab in the AWS console, to get the created role ARN. In the Cloud One - Application Security Cloud Formation stack view, add the role ARN in the ARN Role text box. Then select Next.
Once the role is created, Application Security can access the Lambda functions configuration and provide the security assessment for the serverless functions. The update between Application Security and the AWS account is synced every 10 minutes.
Assess and improve security assessment
Upon setting the access to the AWS account configuration, Application Security processes the Lambda function configuration, and reports on three key aspects:
-
The assessment of Lambda functions configured in the AWS account
-
The association of Lambda functions with the protection groups created in Application Security
-
An overall protection status

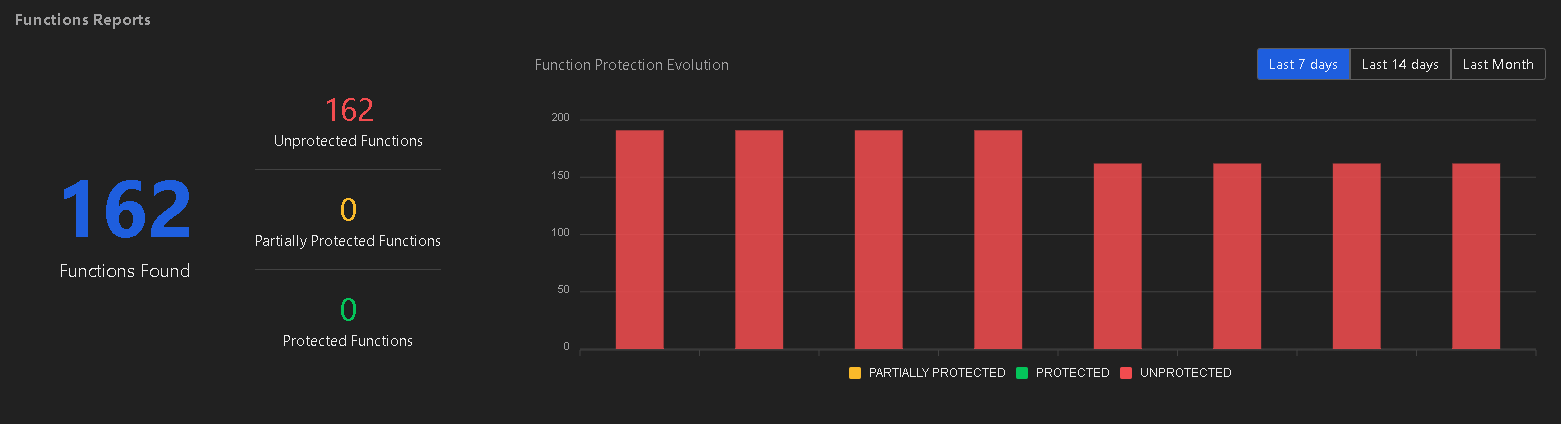
Assessment of Lambda functions protection
At the forefront of the security assessment is the assessment of protection of the Lambda functions provisioned in the AWS account. Application Security queries the AWS account for Lambda functions configuration. The protection status of each function is assessed with one of the following security status:
-
Unprotected. Functions either are not configured with Application Security protection runtimes, or are configured with protection runtimes but with all security controls disabled.
-
Partially protected. Functions are configured with Application Security protection layers or runtimes. Some of the protection types in the security controls are set to report.
-
Protected. Functions are configured with Application Security protection layers or runtimes. All enabled protection types in the security controls are set to mitigate.
Application Security does not enforce that all protection types are enabled as sometimes there are technical reasons that require disabling.
- Exempted. (Optional) Functions that have been marked as Exempted. They are only displayed if Include Exempted Functions is enabled.
Association of Lambda functions with protection groups
Once functions are configured to be protected by Application Security protection runtimes, and the protection runtimes become active, Application Security can associate the Lambda function with the protection group.
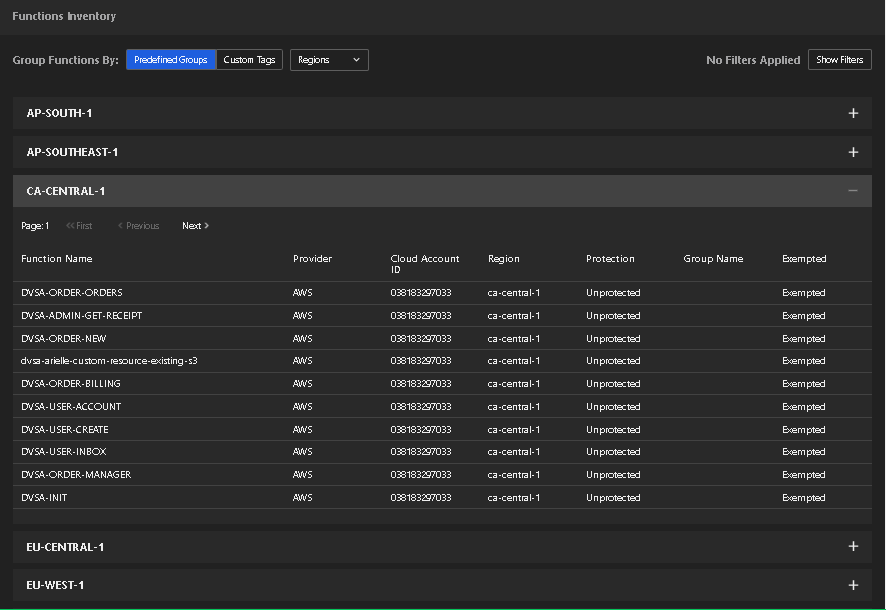
The Lambda functions can be grouped and presented by three attributes:
-
AWS regions
-
Protection status: that is grouped by Protected, Partially Protected or Unprotected status
-
By Application Security protection groups
Filters can also be applied with the same three attributes:
-
AWS regions
-
Protection status: that is grouped by Protected, Partially Protected or Unprotected status
-
By Application Security protection groups
Together, the grouping and filtering can be leveraged to quickly and easily view the Lambda functions that are unprotected and need attention. For example, by grouping and filtering by protection status, the unprotected Lambda functions can be quickly reviewed.
Likewise, by grouping by protection groups, the list of Lambda functions associated with a protection group can be easily identified.
Overall protection status
The Application Security security assessment provides an overall protection status across all Lambda Functions across all regions and protection groups. The overall protection provides an quick and easy view of the overall protection status across all functions.