Topics on this page
Open redirect
Open redirect attacks are most commonly used in phishing attempts by redirecting a user to a new website without any validation of the target of redirect. Application Security protects your application by only allowing redirects that you have explicitly allowed.
Configure the open redirect policy
- Select the group.
- In the left pane menu, click
 .
. - Ensure that Open Redirect.
- Set the state to Report. This will trigger events without blocking the request, which allows you to run your application and see which expected behaviors trigger Open Redirect events.
- On the right of the page,click
 .
. -
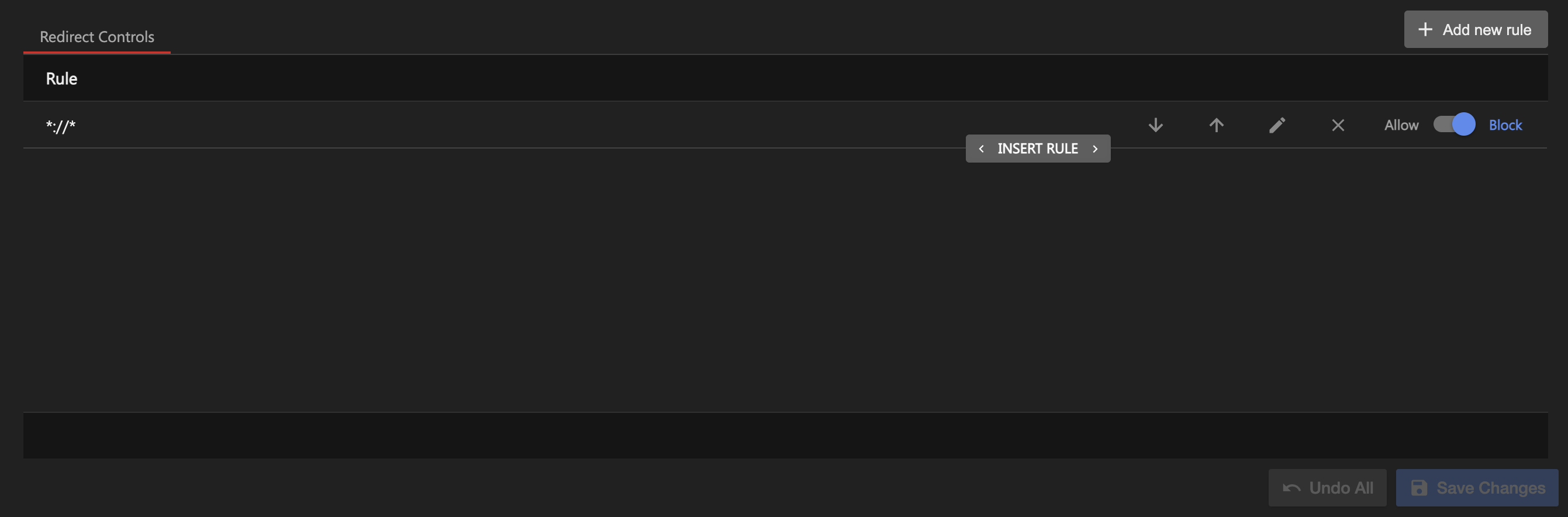
Under Redirect Controls is the default rule
*://*.
By default,
*://*is set to Block. This blocks fully qualified domain redirects but not relative redirects. -
Close the Open Redirect Policy Configuration window.
-
Navigate to your application and use it in the various scenarios that it was designed to handle.
- On the Application Security dashboard, check the Events page for Open Redirect events. If one has been triggered, follow the steps in Manage Open Redirect events.
- Once you're happy with your policy configuration and events are no longer being triggered by expected behavior, go to Your Group > Policies > Open Redirect.
- On the right of Open Redirect, set the state to Mitigate. When a rule is triggered, the attempt will be blocked and an Open Redirect event will appear on the Dashboard.
Add a new open redirect rule
Policy rules are processed from the top down and if there is a match the rule is applied. Therefore, all Allow rules should be ordered above Block rules.
- Select Add new rule button on the right of the Open Redirect Policy Configuration window.
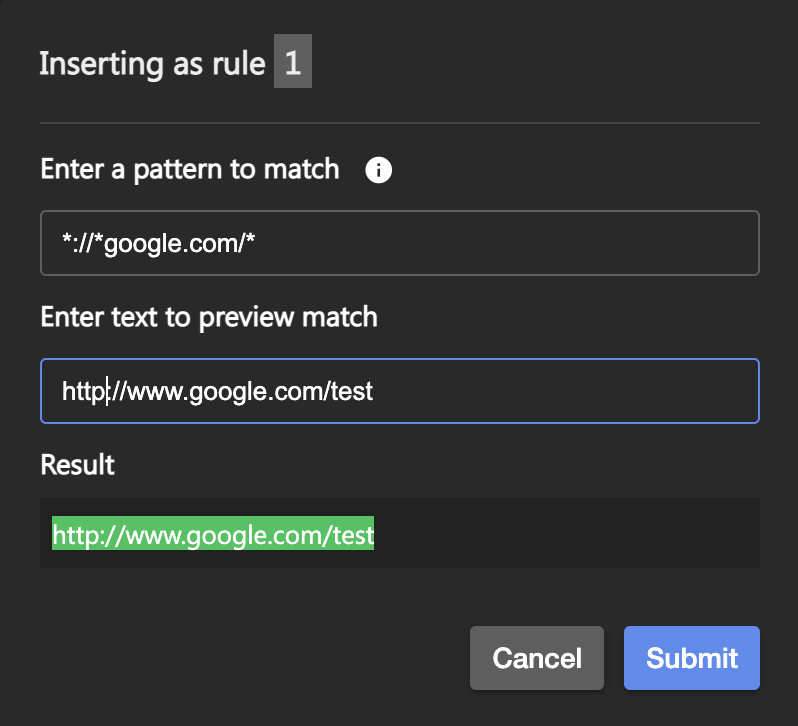
- Under Enter a pattern to match, enter the glob pattern that matches your URL.
- Under Enter text to preview match, enter the actual URL you want protected. If the glob pattern you entered above is the correct pattern and encompasses the URL, the URL will be highlighted in green under Results. If the URL is grey, correct your glob pattern.
-
Select Submit to save the rule. By default, the rule will be set to Allow.
Delete an open redirect rule
- In the row containing the rule to delete, select the X icon.
- Select Save Changes and close the window.
Open redirect events
Open Redirect events are displayed on the Dashboard in Events or in your respective Groups's dashboard.
Every event includes the Request Details panel for general information about the event. For more information, see Manage Events.
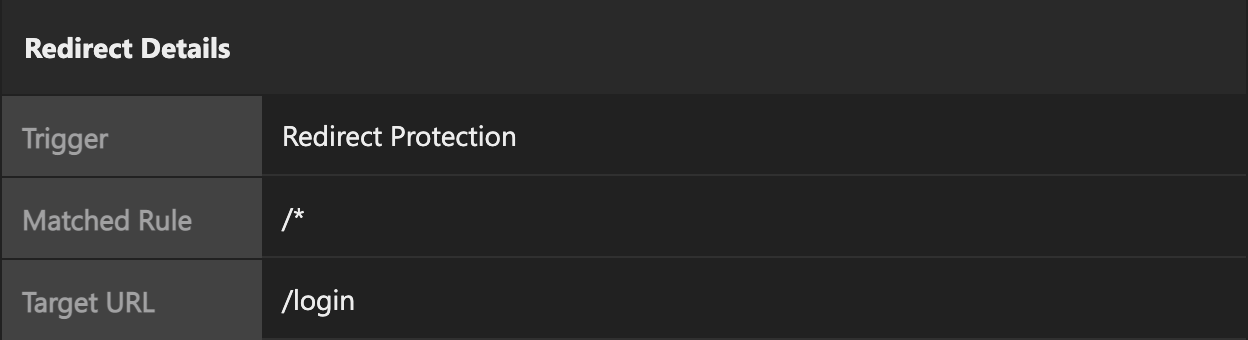
Under Redirect Details, the following information is displayed:
- Trigger: The reason the Open Redirect event was triggered
- Matched rule: The rule that was matched and triggered an Open Redirect event
-
Target URL: The URL attempting to be redirected
Manage open rdirect events
If Application Security is reporting Open Redirect events:
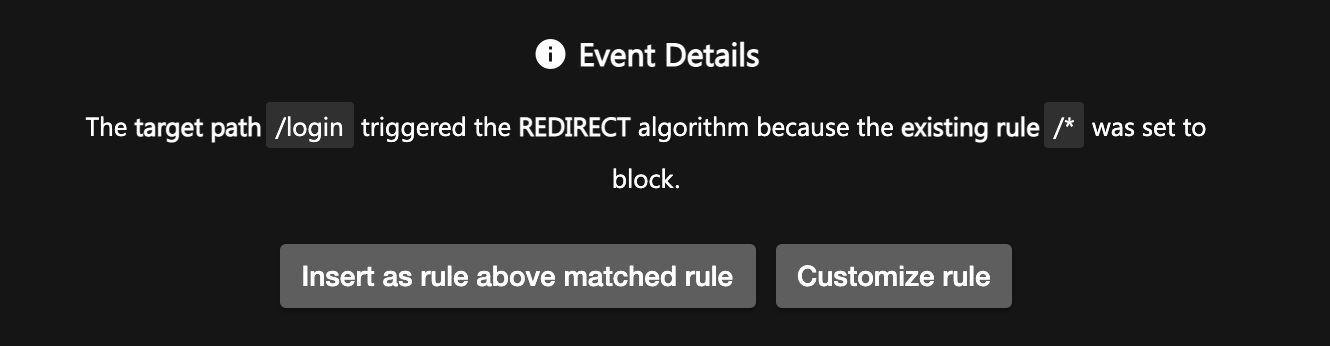
- In the top-right corner of the event details panel, select View Stack to see where in your code the attack was leveraged. Modify your code so an Open Redirect attack can't be leveraged in the future.
-
If the event was triggered by an expected behavior of your application and you'd prefer not to modify your code and allow the behavior, select Click to Manage Policy. In the Alert section, you can see the target path and the existing rule that triggered the event. Select Insert as rule above matched rule to automatically add the glob pattern for the URL. This will create an allow rule. If you'd like to edit the glob pattern, select Customize rule and Submit when you're finished.