Topics on this page
Use Application Security layer to protect AWS Lambda functions
Application Security provides security layers for protecting AWS Lambda functions. The security layers includes all the security controls for Lambda functions self protection.
This is supported only by Python and Node.js programming languages.
Adding protection to your Lambda function is simple and only requires adding the Application Security layer and adding the required configuration for the handler and the security layer. The installation and configuration are dependant on the function programming language and on the version of Amazon Linux.
Configure the protection layer in AWS Lambda
- In your AWS account, go to Lambda > Functions and select the function you'd like to protect.
- In the Function Overview, select Layers to be taken to the layers configuration view.
-
Select Add layer. On the Choose a layer view, select Specify an ARN. Specify the Application Security protection layer ARN in the text box Specify an ARN. Find the appropriate ARN in Python layers for AWS Lambda or NodeJS layers for AWS Lambda.
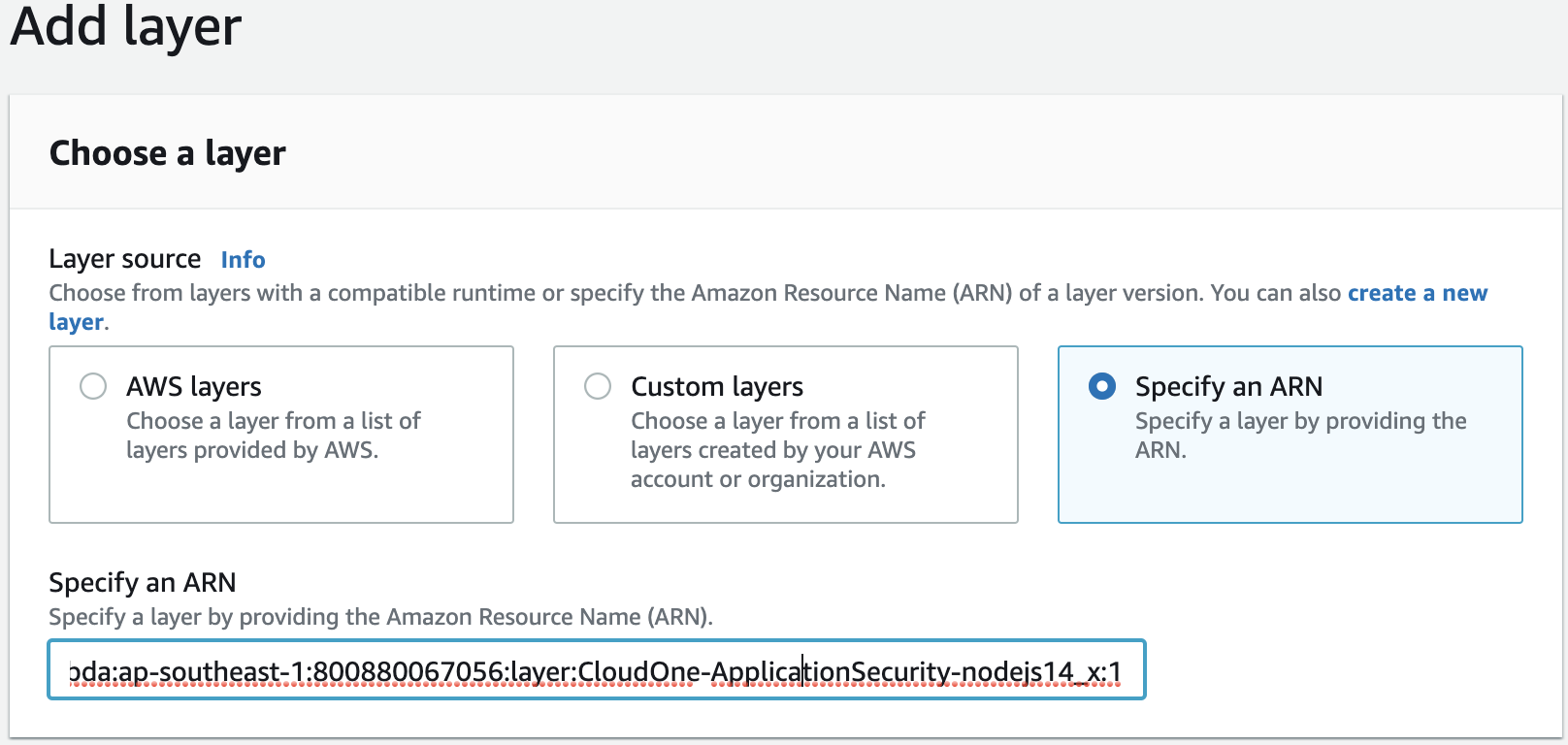
-
Configure the required Runtime:
-
From the function overview, scroll to the Runtime settings panel, then select Edit, then select the required Runtime from the menu. Note that the layer and runtime selected must be the ones related to the function's programming language.
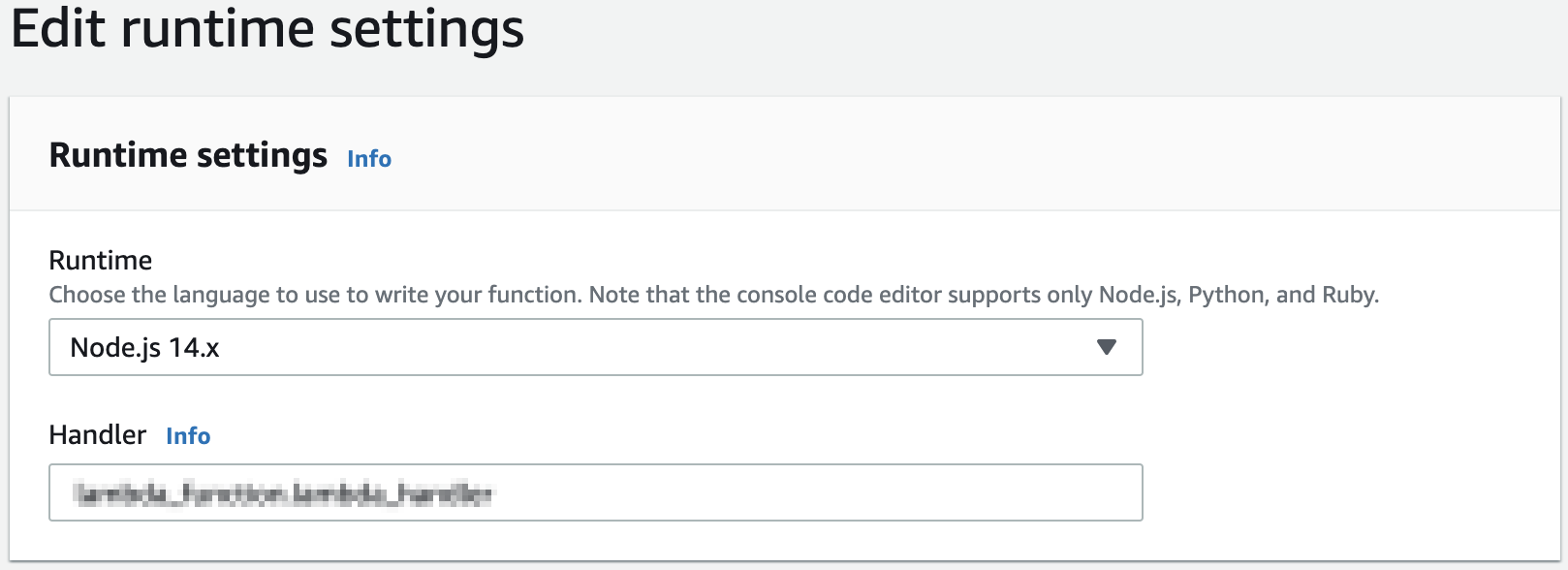
-
The configuration to enable the security layer and for the handler, depend on the function programming language and the Amazon Linux version.
Connectivity for multi-region aware agents
Recent agent versions include the multi-region aware connectivity, which enables the agents to automatically determine which region to connect. For those agents, there is no need to add additional configuration in the agent, that is the hello_url configuration parameter doesn't need to be added to the agent configuration. The multi-region aware connectivity module in the agents enables the agent connections to be redirected to the right region when the closest region is not the right one. For more information, see Leverage Application Security in different regions
Currently the only versions of the agents that do not require the 'hello-url' configuration are Python agent 4.6.2 and Java 4.4.4.
Configure the handler for Python 3.8 on Amazon Linux 2
To configure the handler, when using python 3.8 on Amazon Linux 2, set the following environment variable to the given value:
AWS_LAMBDA_EXEC_WRAPPER=/opt/trend_app_protect<filename>.<function name>. Refer to AWS' documentation for more details.
Configure the handler for Python versions prior to 3.8, on Amazon Linux
When running Python 3.7 on Amazon Linux, the handler needs to be set up to call the Application Security handler, which in turn will call your function handler. Do the following: 1. Set the handler to trend_app_protect_handler.handler 2. Set the environment variable to your function handler:
TREND_AP_HANDLER=<filename without extension>.<function name>This environment variable should be set to the Lambda's original handler. Depending on the Lambda handler, you may have to use TREND_AP_HANDLER=<filename_without_extension>.<function name> instead.
Configure the handler for any versions of NodeJS
To configure the handler, when using any versions of NodeJS, set the following environment variable:
AWS_LAMBDA_EXEC_WRAPPER=/opt/trend_app_protect<filename>.<name of the exported handler module>. Refer to AWS' documentation for more details.
-
In order for the Application Security layer to protect your function, the Application Security group Key and Secret need to be configured as environment variables, for your function. In the Environment variables section, enter the values as seen in the below screenshot.
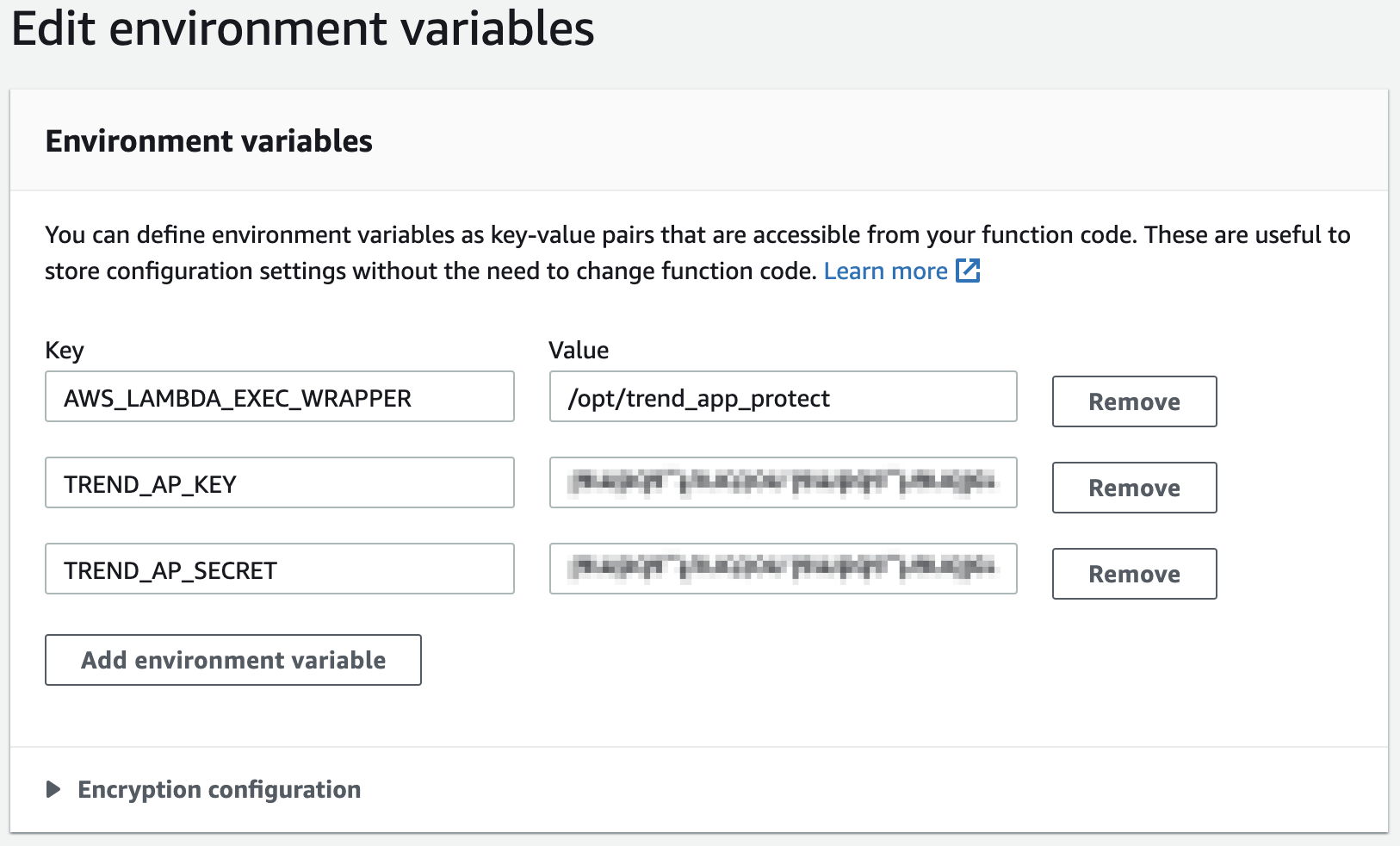
To find your Application Security group Key and Secret, go to the Application Security dashboard and navigate to your group's setting page. The Key and Secret are displayed under Group Credentials.
Amazon Resource Names (ARNs)
The Application Security protection layer is available in multiple AWS regions.
The protection layer ARN depends on the lambda function programming language and the language version. The ARN structure for the protection layer is:
arn:aws:lambda:<aws region>:800880067056:layer:CloudOne-ApplicationSecurity-<language>:<layer version>aws region = eu-north-1, ap-south-1, eu-west-1, eu-west-2, eu-west-3, ap-northeast-1, ap-northeast-2, ap-southeast-1, ap-southeast-2, sa-east-1, ca-central-1, eu-central-1, us-east-1, us-east-2, us-west-1, or us-west-2
Languages versions for AWS Lambda protection layer
| Language | Layer Version | Description |
|---|---|---|
| python | 1 | For python 3.7 and 3.8 |
| nodejs10_x | 1 | For NodeJS 10 |
| nodejs12_x | 1 | For NodeJS 12 |
| nodejs14_x | 1 | For NodeJS 14 |
For example: If a lambda function is deployed in region us-east-1 and implemented with Python 3.7, the ARN is:
arn:aws:lambda:us-east-1:800880067056:layer:CloudOne-ApplicationSecurity-python:1Additional configuration for Lambda on AWS official runtimes
When using the Application Security protection layer, some additional configuration needs to be set as environment variables. Add the following in addition to the TREND_AP_KEY and TREND_AP_SECRET

TREND_AP_KEY: < key from Application Security Dashboard >
TREND_AP_SECRET: < secret from Application Security Dashboard >
TREND_AP_READY_TIMEOUT: 30
TREND_AP_TRANSACTION_FINISH_TIMEOUT: 10
TREND_AP_MIN_REPORT_SIZE: 1
TREND_AP_INITIAL_DELAY_MS: 1
TREND_AP_MAX_DELAY_MS: 100
TREND_AP_HTTP_TIMEOUT: 5
TREND_AP_PREFORK_MODE: False
TREND_AP_CACHE_DIR: /tmp/trend_cache
TREND_AP_LOG_FILE: STDERRFor more information about configuring environment variables, see Environment variables.