Topics on this page
Integrate Trend Micro Artifact Scanner results into your policies
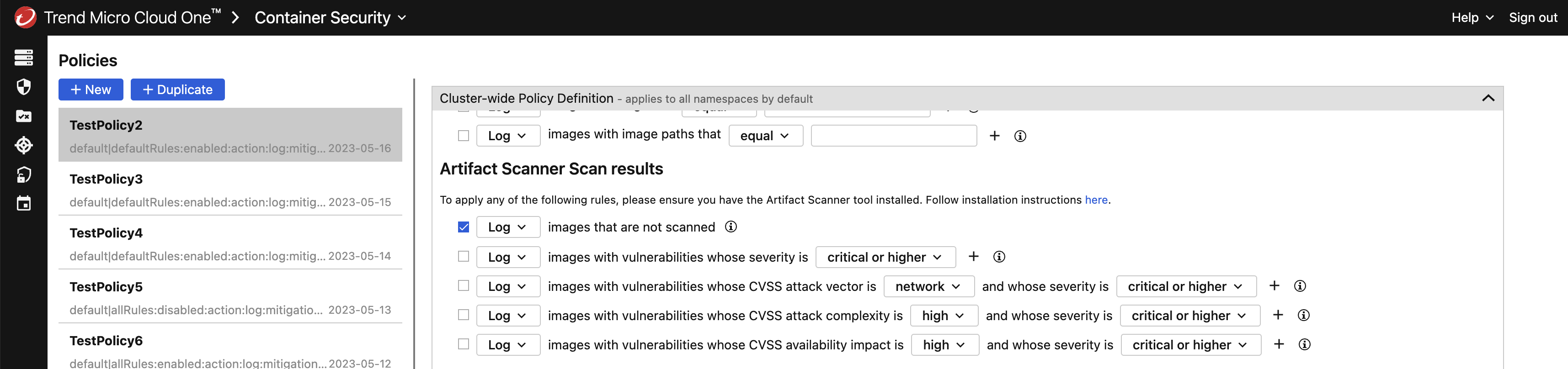
You can integrate your Trend Micro Artifact Scanner results into your Container Security admission control policies. For information on how to install and setup the CLI, see About Trend Micro Artifact Scanner.
The scan result is automatically sent to Cloud One Container Security. However, you must scan using the registry artifact type (registry:yourrepo/yourimage@digest) to be able to use the results.
For example:
tmas scan registry:nginx@sha256:08e9c086194875334d606765bd60aa064abd3c215abfbcf5737619110d48d114 --region us-1 -VM
This pulls the image from your registry, generates an SBOM, and performs an open source vulnerability and malware scan.
When deploying a container into a cluster, specify the image digest for the image you wish to deploy. This digest is generated when the image is pushed to a registry and should also be used when scanning images with Trend Micro Artifact Scanner. This allows scan results to be automatically correlated with the images being deployed into the cluster.
Although Trend Micro Artifact Scanner supports scanning multiple-architecture (multi-arch) images, only one image from the manifest list is scanned when a multi-arch image digest or tag is specified. The scanned image is chosen based on the platform flag, with the default scanned architecture being linux/amd64. Scan results are architecture-specific to ensure that the assessed vulnerabilities are tailored to a selected architecture.
Using multi-arch tags or digests to scan and deploy images introduces a security risk if the cluster has nodes with different architectures than what was scanned.
To accurately evaluate the risks and threats associated with image deployment, provide the architecture-specific digest when scanning an image and deploying it into your cluster. This ensures that the scanned image matches what will be deployed into your cluster.
This correlation allows you to easily configure an admission control policy. For example, you could block any container images which have CRITICAL vulnerabilities from being deployed into your clusters.
Trend Micro Artifact Scanner's scan results are only valid for admission control policy for 30 days after the scan is completed. After this period, the image is treated as if it was not scanned. If using Cloud One Container Security admission control policy, you must scan the same image at least once every 30 days. This ensures that admission control decisions are based on relatively recent vulnerability and malware findings.
Next, you need to create a policy.