Topics on this page
Configure runtime security
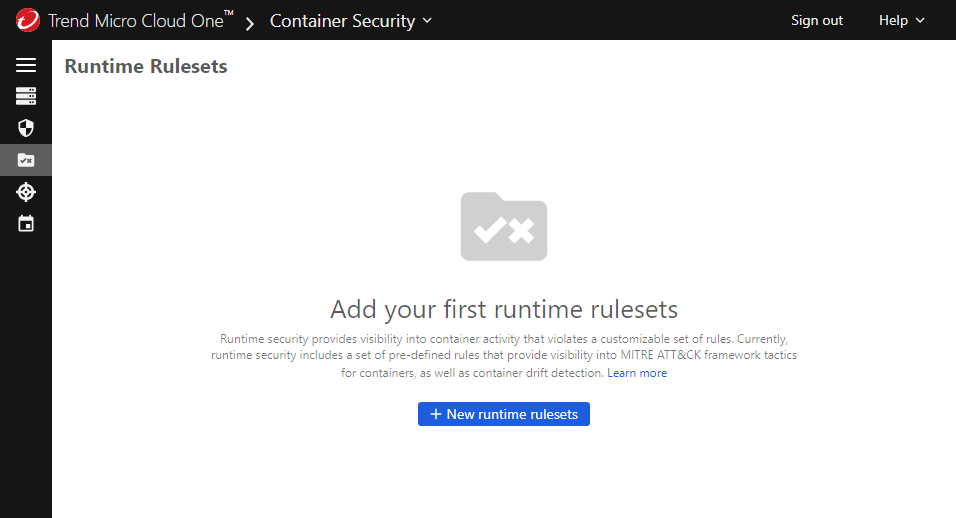
Runtime security provides visibility into container activity that violates a customizable set of rules. Currently, runtime security includes a set of pre-defined rules that provide visibility into MITRE ATT&CK framework tactics for containers, as well as container drift detection. Container Security can automatically mitigate problems detected by the runtime security feature. If a pod violates any rule during runtime, the issue is mitigated by terminating or isolating the pod based on the ruleset assigned to its Container Security policy.
Runtime security is compatible with Kubernetes and supports Amazon EKS, Microsoft Azure AKS, Google GKE, and OpenShift. It is currently supported with default and the most recent Linux kernels.
Create a runtime ruleset
After you have access to the runtime security preview, create one or more runtime rulesets. Choose from several managed rules provided by Trend Micro to define a set of rules that you want to enforce.
- Open the Trend Cloud One console and select Container Security.
- Go to
 Runtime Rulesets.
Runtime Rulesets. -
Do one of the following:
-
If this is your first ruleset, click + New runtime rulesets.
-
If this is not your first ruleset, select + New.
-
-
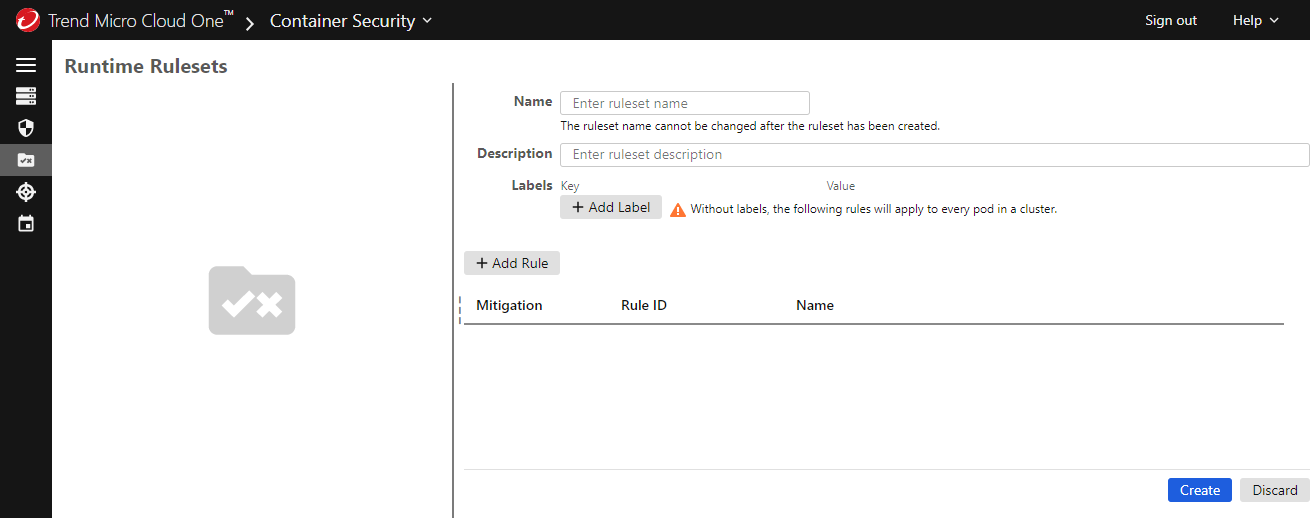
Provide the following information:
- Name: a unique name for the ruleset that will help you to identify it. You cannot change this name after the ruleset is created.
- Description: an optional description of the ruleset.
-
By default, the ruleset is applied to all pods in a cluster. If you want to limit the ruleset to certain applications, add one or more labels that match against the Kubernetes labels applied to your applications. Container Security enforces the rules for applications that match the labels you specify:
- Click Add Label.
-
Enter the label key and value to be matched.
For example, adding a label of
app:phpapplies the ruleset only to Kubernetes pods labeled withapp:php.
-
Click Add Rule and use the dialog to select the rules that you want to enforce with this ruleset, then click Apply. To select all rules, use the table heading.
For information about the attack technique that a rule is designed to prevent, search for the MITRE ID (for example
T1021.004) at MITRE ATTACK. -
For each rule, use Mitigation to select the action that Container Security takes when a running pod violates the rule. These actions include logging an event and allowing the pod to keep running, isolating the pod's network traffic, and terminating the pod.
-
Click Create to finalize your new ruleset.
Add a ruleset to a policy
Create a policy and use the Runtime tab to add one or more rulesets to it. You can also add rulesets to an existing policy. For instructions, see Create a policy.
You also need to assign the policy to the cluster that you want to protect. This applies the ruleset to the cluster.
Enable runtime security for a cluster
If you have not registered a cluster to Container Security, follow the instructions in Add a cluster.
If you registered a cluster to Container Security, but did not enable runtime security, proceed as follows:
-
Add
runtimeSecurity.enabled=trueto your overrides file (typically,overrides.yaml):cloudOne: apiKey: <API_KEY> endpoint: <ENDPOINT> runtimeSecurity: enabled: true -
Use the following command to upgrade Container Security:
helm upgrade \ trendmicro \ --namespace trendmicro-system --create-namespace \ --values overrides.yaml \ https://github.com/trendmicro/cloudone-container-security-helm/archive/master.tar.gz
View runtime events
When a runtime rule is triggered, it generates an event visible through the Events page. For more information, see Monitor events.
Disable runtime security
To disable runtime security in a cluster, but keep the other aspects of Container Security, do the following:
-
Set
runtimeSecurity.enabled=falsein your overrides file (typicallyoverrides.yaml).cloudOne: apiKey: <API_KEY> endpoint: <ENDPOINT> runtimeSecurity: enabled: false -
Use the following command to upgrade the Container Security cluster:
helm upgrade \ trendmicro \ --namespace trendmicro-system \ --values overrides.yaml \ https://github.com/trendmicro/cloudone-container-security-helm/archive/master.tar.gz
Taints and tolerations
Taints are a Kubernetes concept that allow nodes to repel a set of pods. For more information, see Kubernetes: Taints and Tolerations. If you are using taints, you can use tolerations to ensure that runtime security is applied to tainted nodes. This is done by adding tolerations to your overrides file in the following format:
tolerations:
scout:
- key: "key1"
operator: "Equal"
value: "value1"
effect: "NoSchedule"To add tolerations for all taints (applying runtime security to all nodes, regardless of taints), add the following to your overrides file:
tolerations:
scout:
- key: ""
operator: ExistsSupported Linux kernels major and minor versions
Container Security Helm version 2.3.14 added support for the modern Berkeley Packet Filter (BPF), also known as eBPF CO-RE (Compile Once, Run Everywhere). This allows Container Security to support any Linux kernel version 5.8 or later, as long as BTF types are exposed.
The following is a non-exclusive list of the kernel version flavors supported by Container Security.
| Platform | Major and minor version | Flavor |
|---|---|---|
| Amazon Linux 2 | 4.14.x | |
| Amazon Linux 2 | 5.4.x | |
| Amazon Linux 2 | 5.10.x | |
| Amazon Linux 2 | 5.15.x | |
| Red Hat Enterprise Linux CoreOS (RHCOS) | 4.18.x | |
| Ubuntu | 4.15.x | generic |
| Ubuntu | 5.4.x | generic |
| Ubuntu | 5.4.x | azure |
| Ubuntu | 5.4.x | aws |
| Ubuntu | 5.4.x | gke |
| Ubuntu | 5.11.x | generic |
| Ubuntu | 5.11.x | azure |
| Ubuntu | 5.11.x | aws |
| Google Container-Optimized OS (COS) | 5.4.x | |
| Google Container-Optimized OS (COS) | 5.10.x | |
| Debian 11 | 5.10.x | generic |
| Bottlerocket | 5.10.x |