Topics on this page
About Cloud Sentry
Cloud Sentry rapidly surfaces malware and provides integrity monitoring detection in your environment without any impact to running applications and resources. Daily scans are performed for trial and paid customers. Cloud Sentry offers visibility of your daily security view of your cloud account.
Cloud Sentry deploys as a serverless scanner in your cloud account to scan your resources for threats. When you deploy Cloud Sentry, it automatically starts scanning the following resources across available AWS regions: EC2 instances, ECR repositories, and Lambda functions. It only returns findings to Trend Cloud One Central by AWS account; you maintain ownership and control of your data and it never leaves your environment.
The Cloud Sentry engine performs a series of functions without an instance to maintain. It is deployed by the CAM cloud formation template. As a serverless function, the Cloud Sentry engine only activates during scanning and can leverage its scalability advantage while performing the scan. Your data remains in the your account. The data is analyzed locally, and only the metadata is processed by Trend Micro backend systems.
Architecture and flow
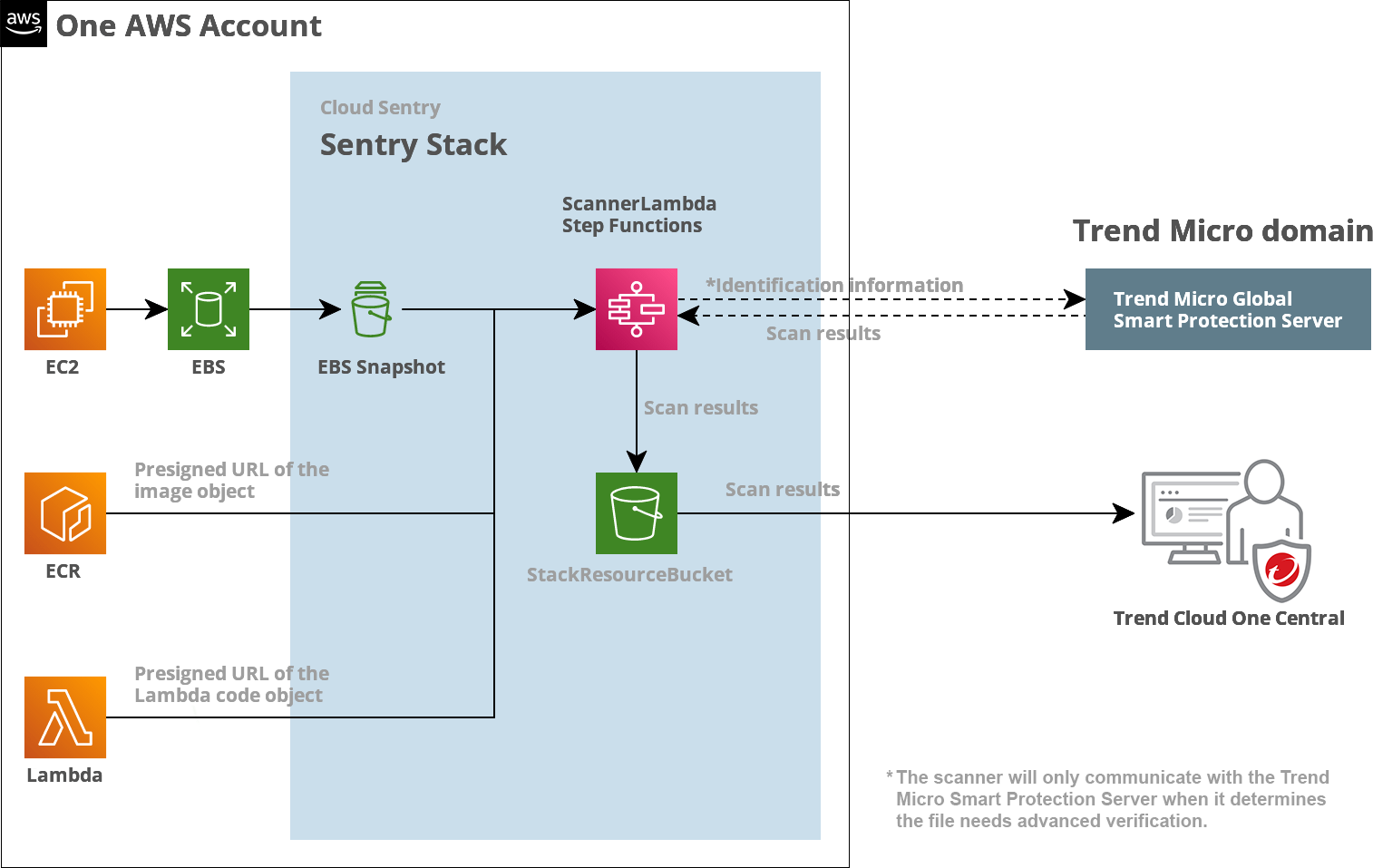
-
Cloud Sentry takes a snapshot of your EBS.
-
It then scans the snapshot. One snapshot is kept for differential comparison.
-
Your data remains in the your account. The data is analyzed locally, and only metadata is processed by Trend Micro backend systems.
-
The results are sent to Cloud One Central where you can view them and their suggested remediation options.
Cloud Sentry provides the following types of threat detection:
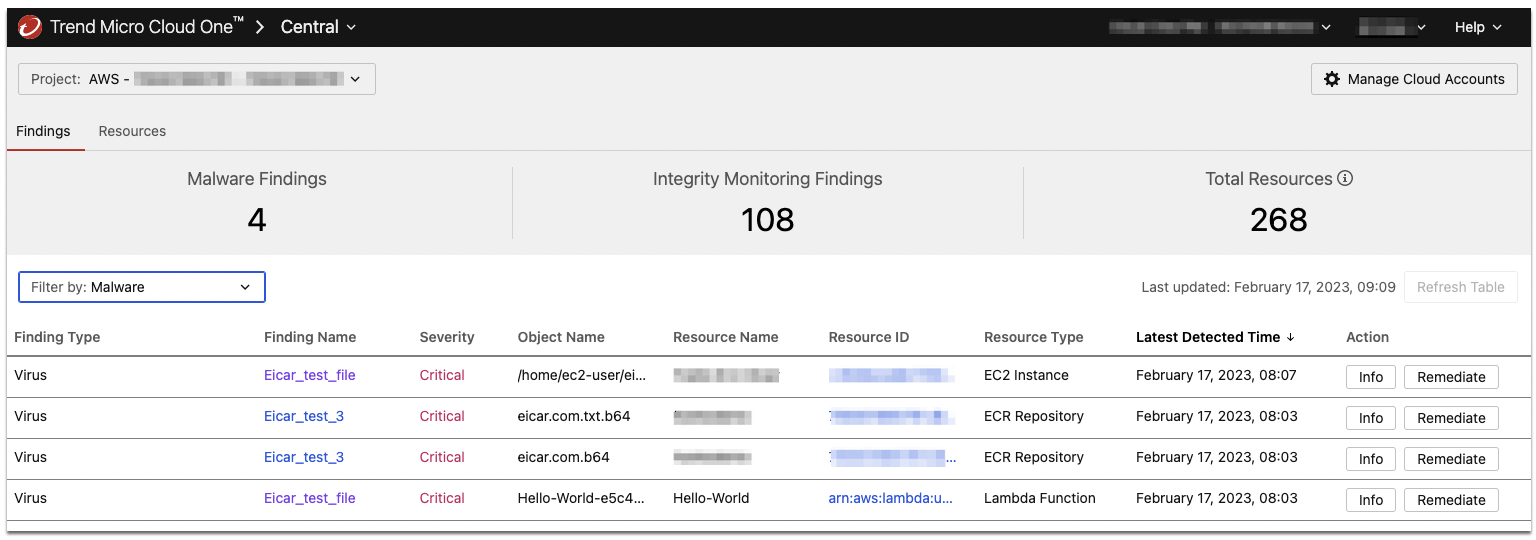
- Anti-Malware. It inspects your EC2 instances, ECR images, and Lambda functions for malware, including viruses, trojans, spyware, and more. The engine is also able to search for obfuscated or polymorphic variants of malware, based on fragments of previously seen malware and detection algorithms. There is no file type or size limitation for the Cloud Sentry scanner.
- Integrity Monitoring. It monitors for suspicious changes in the host operating system of your EC2 instances, including the addition of suspicious artifacts and indicators of attack (IoA).
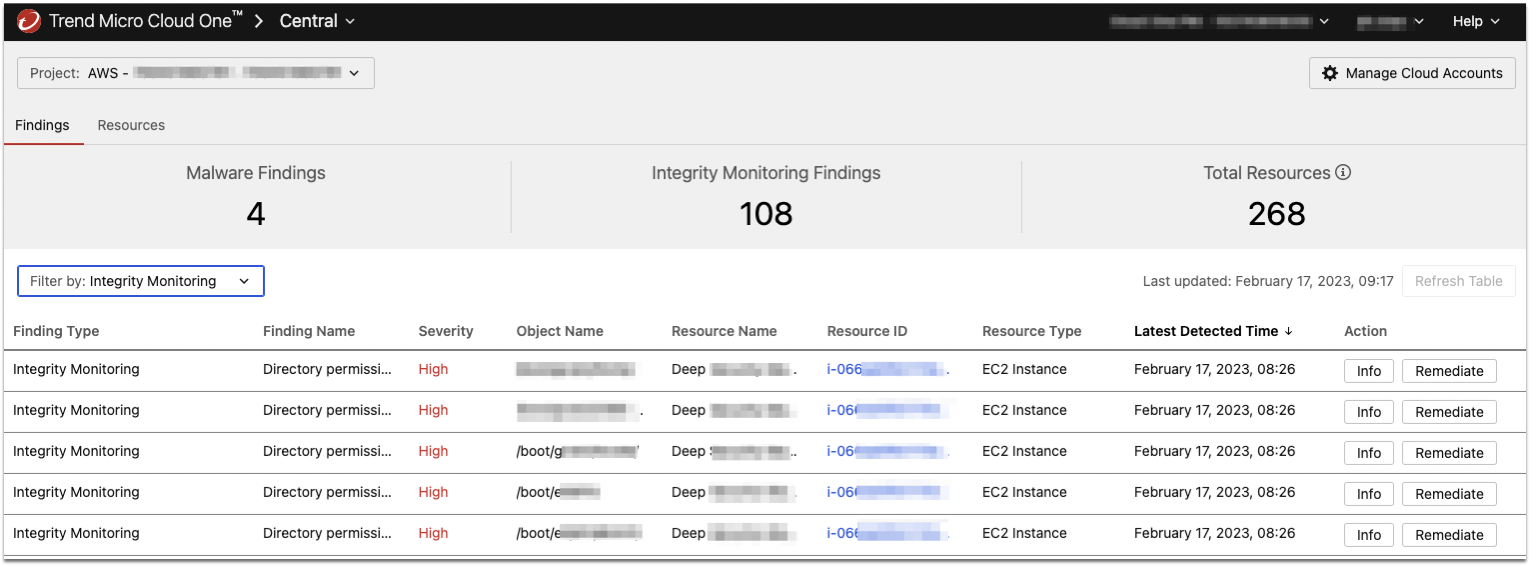
After deployment, Cloud Sentry begins scanning your EBS volumes, ECR container images, and Lambda functions. When findings are detected they are sent to Cloud One Central where you can view them and their suggested remediation options.
Cloud Sentry runs scans on a fixed daily schedule. Scan times may vary depending on the number of resources. However, you should expect findings to start appearing within minutes of the deployment.
Scanned artifacts
Currently, Cloud Sentry scans the following:
-
EBS: Volumes attached to any EC2, NTFS, or Linux instance
-
ECR:
- Images located in private ECR repositories
- Images tagged latest
- Images in tar format
-
Lambda: Functions with deployment packages as .zip file archives
Currently Cloud Sentry is only available for AWS. Other platforms such as Azure and GCP will be supported in the future.
Supported Amazon regions
Cloud Sentry supports the following Amazon Web Services (AWS) regions:
| Region code | Region name (Location) |
|---|---|
| us-east-1 | US East (N. Virginia) |
| us-east-2 | US East (Ohio) |
| us-west-1 | US US East (N. California) |
| us-west-2 | US West (Oregon) |
| af-south-1 | Africa (Cape Town) |
| ap-east-1 | Asia Pacific (Hong Kong) |
| ap-northeast-1 | Asia Pacific (Tokyo)) |
| ap-northeast-2 | Asia Pacific (Seoul) |
| ap-northeast-3 | Asia Pacific (Osaka) |
| ap-south-1 | Asia Pacific (Mumbai) |
| ap-southeast-1 | Asia Pacific (Singapore) |
| ap-southeast-2 | Asia Pacific (Sydney) |
| ca-central-1 | Canada (Central) |
| eu-central-1 | Europe (Frankfurt) |
| eu-north-1 | Europe (Stockholm) |
| eu-west-1 | Europe (Ireland)) |
| eu-west-2 | Europe (London)) |
| eu-west-3 | Europe (Paris) |
| sa-east-1 | South America (São Paulo) |
Cloud Sentry does not support the following Amazon Web Services (AWS) regions due to a lack of a pattern layer:
| Region code | Region name (Location) |
|---|---|
| ap-southeast-3 | Asia Pacific (Jakarta) |
| eu-south-1 | Europe (Milan) |
| me-central-1 | Middle East (UAE) |
| me-south-1 | Middle East (Bahrain) |
Limitations
There is a number of limitations you should consider when using Cloud Sentry.
Amazon Elastic Block Store (EBS) snapshot limit
AWS accounts limit the total pending EBS snapshot count to 100. The Cloud Sentry scanner creates EBS snapshots for all EBS volumes that are attached to the EC2 instances daily. During the creation process, you may encounter a PendingSnapshotLimitExceeded error when creating the snapshots. This may slow in the scanning.
Cloud Sentry stack removal error
If you have a specific stack version and try to remove the Cloud Sentry stack from your AWS account, you may encounter the DELETE_FAILED at StackResourceCleanerCustom with AccessDenied error preventing removal of the stack. Although this issue was fixed in the latest version of the Sentry stack, you might still experience it if you are on the previous stack. You can troubleshoot it as follows:
-
In AWS CloudFormation, navigate to Stacks > StackSet-SentrySetNNN-NNN > Events. Notice that Status is displayed as DELETE_FAILED with Status reason StackResourceBucketCleanerCustom AccessDenied.
-
Select Resources and enter StackResourceBucket in the search field.
-
Locate both StackResourceBucketCleanerLambdaRole and StackResourceBucketLogsCleanerLambdaRole under Logical ID.
-
Under Physical ID, click the arrow icon corresponding to both physical IDs to access their IAM role definitions.
-
In IAM > Roles > Permissions > Permission policies, select NNN-StackResourceBucketLogsCleanerFunction permission under Policy name.
-
Use the Policy editor to add the following necessary permissions to enable the list s3 version:
"Statement": [ { "Action": [ ... "s3:ListBucketVersions", "s3:GetObjectVersion", "s3:GetBucketVersioning" ], ... -
Click Next.
-
On Review and save, click Save changes.
-
If the error occurs in other regions, replicate the same changes in the corresponding regions.
-
In Stacks, select the parent stack and click Delete to initiate the removal of all stacks, including the SentrySet stack, across all deployed regions.
-
In the Delete stack? dialog, click Delete without selecting any offered options. This removes all stacks and resources, including s3 buckets and StackResourceCleanerCustom deployed for Sentry.
Deployment
You can enable or disable Cloud Sentry when you add or update your AWS accounts on your Cloud Account Management page. For more information, see Manage your AWS cloud accounts
Upgrade from preview version to release version
The release date for the general availability of Cloud Sentry is 2023/03/01. If you are using the preview version of Cloud Sentry, you need to update to the latest version to get rid of the hourly error log in CloudWatch.